The spread of the ransomware has brought serious security threats to enterprises and individuals. 360 Security Center provides comprehensive monitoring and defense against ransomware. Based on this month’s data, the amount of anti-ransomware feedback has increased significantly, among them Stop ransomware family are with the highest feedback.
In March, 360 Decryption tool added decryption support for the five ransomware families of JsWorm 4.0.3, Nemsis (modified suffix Wecanhelp), Planetary (modified suffix haka), ECh0raix, and Spades.
Infection data analysis
Compared with the July data, this month’s anti-ransom service feedback has increased significantly, and the amount of Stop feedback has risen the most. GlobeImposter released a new variant with Simplified Chinese this month. The Sodinokibi attack gang has also started targeted phishing email attacks against Chinese users. Nemty’s new ransomware, which mimics Sodinokibi, began to spread in China.
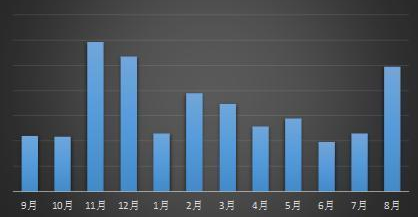
Recent 12 months of ransomware feedback statistics
According to the analysis of the proportion of the ransomware family this month, the Stop family ranked first with 36.83%, followed by the phobos family with 20.08%, and the GlobeImposter family ranked third with 15.44%.
The proportion of ransomware families in August 2019
The Epidemic Analysis of Ransomware
Sodinokibi ransomware
360 Security Center monitoring, Sodinokibi ransomware appeared a large-scale phishing email spread around August 9th. The e-mail attachments issued by the ransomware communicators began to use Simplified Chinese naming. (The e-mail attachment file names that were previously issued are all traditional characters, and it is speculated that the ransomware may start a round of transmission to mainland China.)
Sodinokibi ransomware spreads through emails in August
The ransomware attacked 22 local governments in Texas this month, claiming a total of $2.5 million in ransom. At the same time, the ransomware was also exposed this month by invading some WordPress sites abroad, injecting JavaScript code for phishing. This attack method is similar to the previous GandCrab camouflage font update. From the communication channel, Sodinokibi has inextricably linked with GandCrab.
Stop
According to the 360 decryption tool data, only for the Stop ransomware in this month, the decryption equipment exceeded 1400 units. Most of the machines that recruited the ransomware are due to downloading cracking software or activation tools from outside the country, causing the files to be encrypted. The ransomware transmission route is single, but due to the channel characteristics, even if it is killed by anti-virus software, there are still a large number of users being attacked.
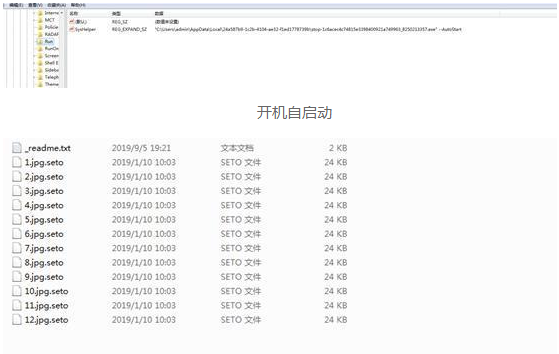
The ransomware virus has undergone a major update this month. The latest update files have been suffixed with geto, seto, peta, etc. This update is mainly enhanced on the encryption algorithm. Previously, it was a key of the same type of file. Now it is a file and a key. At the same time, the ransomware is not directly running to encrypt the file, but is encrypted at the next boot up.
Encrypted file
Nemty
360 Security Center have detected a new ransomware- Nemty in this month, which is spread by manual poisoning after blasting remote desktops. The ransomware information of the Nemty ransomware is extremely similar to the known Sodinokib ransomware. Forum public information shows that the ransomware producer is the maker of the previous JsWorm ransomware, and also uses the RaaS model (full name “Ransomware-as-a-Service”: ransomware as a service). The ransomware producer developed a ransomware virus for cybercrime organizations, and the cybercrime organization was responsible for spreading the ransomware. The two parties divided the ransom according to the cooperation agreement. This model has been adopted by many families, such as the well-known GandCrab, Sodinokibi and FilesLokcer.
JSWorm author’s post
Ouroboros
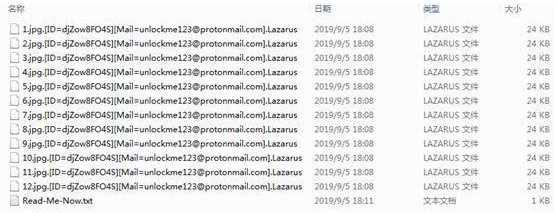
At the end of July, 360 Security Center detected the arrival of the Ouroboros ransomware virus in China. In August, we received multiple victims for help. From the monitoring data, the ransomware virus is currently mainly spread by delivering spam. Most of the ransomware virus family variants currently use the Lazarus suffix (previously limbo and other suffixes), and there are multiple contact mailboxes.
Files encrypted by Ouroboros
Interestingly, the ransomware will establish a connection with www.sfml-dev.org before encrypting the file. If the connection cannot be established, the key encrypted in the program will be used to encrypt the file. If the connection can be established, it will send the locally generated ID to the server, and the server generates a key based on the ID to encrypt the file.
Ouroboros’ built-in key
GlobeImposter
The GlobeImposter ransomware was updated this month. This update mainly made some changes on the extortion prompt information, and added simplified Chinese prompts for Chinese users. At the same time, the extortion prompt information generated in each folder was changed to an executable program and no longer a txt document. The suffix is changed from the previous “Twelve Lords” +666 to “Twelve Lords” + 865. For example, the latest suffixes: Aphrodite 865, Hermes 865, artemis 865, Hades 865, Apollon 865, and the like. (Recently foreign security research institutes refer to the recent variant of GlobeImposter as the Maoloa family. Both use the same extortion information, and the decryption methods are relatively close. The domestic unified name is called the GlobeImposter family).
GlobeImposter ransomware message
Hacker mailbox disclosure
The following is thehacker emails indexed by the 360 blackmail search engine in August 2019:
Server protection data analysis
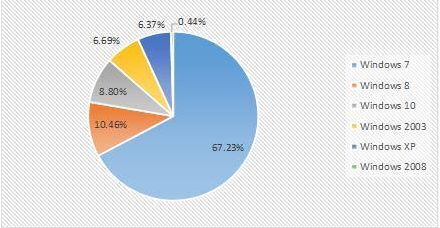
Compared with the previous month’s data, there is no significant fluctuations for the operating system accounted in this month.
The proportion of attacked systems in August 2019
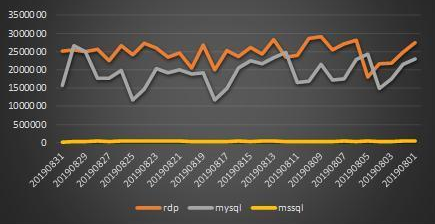
Compared with the previous month’s data, the data in the last two months is relatively stable, and the password blasting attack trend is stable.
Weak password attack trend chart for August 2019
Ransomware keyword
The data is derived from the search statistics of lesuobingdu.360.cn. (excluding WannaCry, AllCry, TeslaCrypt, Satan, and kraken families)
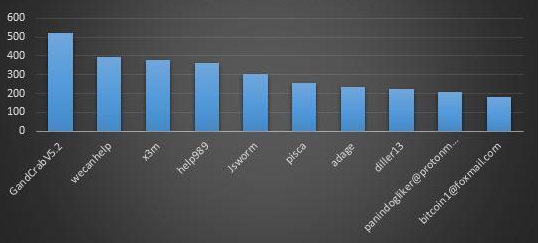
This month, users searched for ransomware keywords for a total of 25,000 searches. Here are the TOP10 search keywords for this month:
- 2: A version of the GandCrab ransomware family. The ransomware was announced to stop updating on June 1st, 2019. The 360 released the decryption tool in the same month. Due to the large number of infections, it has always been a popular search and is currently in the “latest declassified ransomware” list.
- Wecanhelp: A variant of the Nemesis (same X3m) ransomware family, which becomes a keyword because the encrypted file suffix is modified to wecanhelp. The ransomware family mainly spreads remote desktops and successfully spreads after manual poisoning. Poison users can refer to the self-help guide (https://bbs.360.cn/thread-15780698-1-1.html) to find the temp000000.txt file with the key to try to decrypt the file.
- X3m: belongs to the X3m ransomware, which began to appear in June, and the latest popular variant is called Nemesis. Currently on the list of “latest declassified ransomware” list.
- Help989: belongs to the GlobeImposter family and becomes a keyword because the encrypted file suffix is modified to help989. The ransomware family is mainly spread by manual poisoning after blasting remote desktops. The GlobeImposter variant is frequent and has many versions, but the suffix variant has been in a higher popularity in the last two months.
- JsWorm: belongs to the JsWorm ransomware, the 360 decryption tool has supported the decryption of the latest version of the family 4.0.3 this month. Currently on the list of “latest declassified ransomware” list.
- Pisca: belongs to the phobos family and becomes a keyword because the encrypted file suffix is modified to pisca. The ransomware family is mainly spread by manual poisoning after blasting remote desktops.
- Adage: belongs to the phobos family, with Pisca.
- Diller13: belongs to the GlobeImposter family, same with help989
- Panindogliker@protonmail.com: belongs to the phobos family and is a keyword because it contains the mailbox in the encrypted file. The ransomware family is mainly spread by manual poisoning after blasting remote desktops.
- bitcoin1@foxmail.com:same with panindogliker@protonmail.com
TOP10 Ransomware search keyword in August 2019
360 Decryption Tool
From the statistics of the decryption tool in this month, the largest amount of decryption this month is still the GandCrab ransomware, followed by the Planetary family; the highest number of users who use the decryption master to decrypt files is still the Stop family. Followed by the GandCrab family, the amount of decryption has remained high due to long-term transmission in China.
Summary
The ransomware attack against the server is still a major direction of the current ransomware. Enterprises need to strengthen their information security management capabilities—especially weak passwords, vulnerabilities, file sharing, and remote desktop management to deal with the threat of ransomware. Here are some advice for administrator we provide:
- Multiple machines, don’t use the same account and password
- The login password must be of sufficient length and complexity, and the login password should be changed periodically.
- The shared folder of important information should be set to access control and be backed up regularly.
- Regularly detect security vulnerabilities in systems and software and patch them in time.
- Check the server periodically to see if there is an exception. View range includes:
- a) Whether there is a new account
- b) Whether the guest is enabled
- c) Whether there is any abnormality in the Windows system log
- d) Whether the anti-virus software has abnormal interception
Learn more about 360 Total Security