The spread of ransomware has brought serious security threats to enterprises and individuals. 360 Security Center conducts comprehensive monitoring and defense against ransomware. This month, chchbuy and GarrantyDecrypt’s new variant “Bigbosshorse” were added.
360 Decryption Tool added decryption support for multiple variants of Hakbit and Paradise in November. Among them, Paradise’s decryption support includes several variants that have been changed to the following suffixes after poisoning:
- paradise
- exploit
- p3rf0rm4
- immortal
- NewCore
- Prt
- CORP
- VACv2
Analysis of infection data
The percentage of ransomware families this month: the Crysis family accounted for 15.85%, ranking first; the Stop family accounted for 15.18%; the phobos family ranked third with 13.62%. Compared with last month’s data, the Stop family’s share has changed significantly, from 9.52% in October to 15.18% this month.
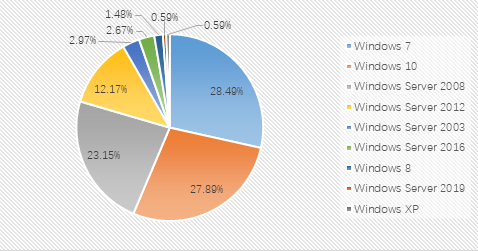
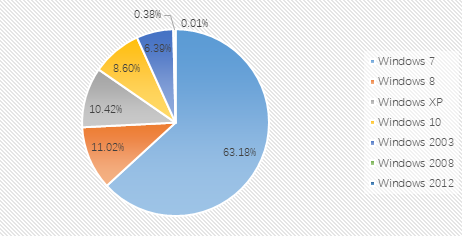
From the proportion of infected systems: Windows 7, Windows 10, and Windows Server 2008 are still the top three systems this month. The proportion of each operating system has not changed much.
The proportion of desktop systems and server systems in the infected systems in November shows that the main attacked systems this month are still desktop systems. Compared with the statistics in October, there is no significant change overall.
In addition, we also followed the user feedback from the ransomware section of the 360 Forum in November (https://bbs.360.cn/forum.php?mod=forumdisplay&fid=7592):
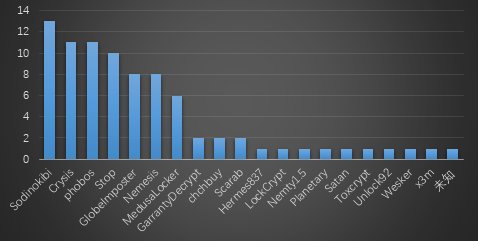
A total of 83 cases were reported in the forum this month, involving a total of 20 ransomware virus families. A total of 5 cases (Unlock92, Nemesis, Nemty1.5, Planetary, x3m) have been supported for decryption families. The feedback family TOP3 is: Sodinokibi (13), phobos (11), and StopV2 (10). New variants included in the feedback include the Hermes837, Crysis and chchbuy families.
In the forum, this month’s ransomware virus family related modules added:
- Ransomware details added: CryptoMix, Ryuk, SpartCrypt, Rapid, DeathRansom, Jigsaw, phobosImposter, CCryptor, chchbuy, GarrantyDecrypt, Dragon, Hakbit
- New ransomware analysis: Ouroboros, MeudsaLocker, chchbuy and Sodinokibi ransomware analysis
Chchbuy ransomware family
In mid-November 2019, 360 Internet Security Center received multiple user feedback that the computer was attacked by chchbuy ransomware virus. The ransomware uses a one-time-one encryption method when encrypting files, that is, each file to be encrypted is encrypted using the Salsa20 algorithm, and only the first 4KB of the file is encrypted.
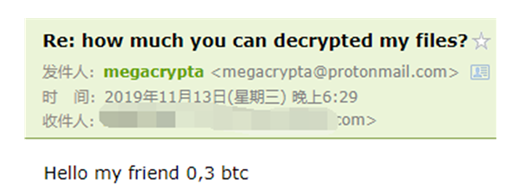
The ransomware left a mailbox in the ransomware prompt, allowing users to actively contact. The communicator asked the victim for 0.3 bitcoin ransom in a reply to the email.
GarrantyDecrypt
The ransomware first appeared in China in January 2019, and at the end of October 2019, 360 Security Center again monitored the ransomware variant. Through the analysis of the victim’s system, it was found that the ransomware violently cracks the user’s remote desktop, and also brute-forced the password of the shared file to gain access to the user’s system. The main hazard of this ransomware is that not only one-time encryption and file type indifferent when encrypting files, the Windows directory is also excluded when encrypting files, and files in other directories will be encrypted. The file extension of encrypted files will be changed to .bigbosshorse.
Satan
360 security Center monitors Satan ransomware, which disappeared for several months, returned to the public eye again on November 4th.This return has the following new features from an attack perspective:
- Added pan-micro OA exploit
- Added remote desktop brute force cracking
- Retain the original horizontal propagation function, such as: eternal blue, double pulsar vulnerability
The following is the hacker email information collected this month:
Chart of the proportion of attacked systems in November 2019:
According to the trend of weak password attack in November 2019, it is found that the attack trend of RDP and MySQL is relatively stable. MsSQL started to stabilize after a sharp rise in October 2019.
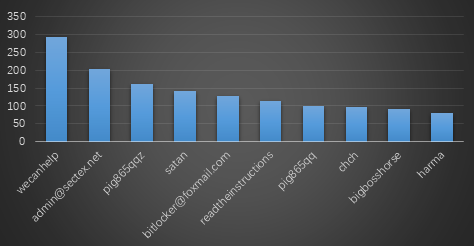
Ransomware Keywords
This data comes from the search statistics of lesuobingdu.360.cn. (Excluding WannCry, AllCry, TeslaCrypt, Satan, Kraken, Jsworm, X3m and GandCrab families)
l Wecanhelp: belongs to the Nemesis ransomware family, which has recently spread through brute force remote desktops. The ransomware generates a temp000000.txt file in the system, which contains the key used to decrypt the file. Generally, it will be deleted by hackers directly, but users of Zhongzhao can try to retrieve the content of temp000000.txt in the following link: https://bbs.360.cn/thread-15780698-1-1.html.
l admin@sectex.net: belongs to the Crysis ransomware virus family. Because files are encrypted, they will be added to admin@sectex.net and become keywords. The ransomware virus family mainly cracked remote desktop passwords through brute force, and then manually transmitted the virus.
l pig865qqz: belongs to the GlobeImposter family, because the encrypted file suffix will be modified to pig865qqz and become keywords. The ransomware virus family mainly cracked remote desktop passwords through brute force, and then manually transmitted the virus.
l satan: belongs to the Satan ransomware virus family. The ransomware currently spreads mainly through vulnerabilities, including pan-micro OA, eternal blue, double pulsar and other vulnerabilities.
l bitlocker@foxmail.com: same as admin@sectex.net
l Readtheinstructions: belongs to the MedusaLocker family, because the encrypted file suffix will be modified to Readtheinstructions and become keywords. The ransomware virus family mainly cracked remote desktop passwords through brute force, and then manually transmitted the virus.
l pig865qq: same as pig865qqz
l chch: belongs to the chchbuy family, because the encrypted file suffix will be modified to chch and become a keyword. The ransomware virus family mainly cracked remote desktop passwords through brute force, and then manually transmitted the virus. The same batch of variants will also modify the file to megac.
l bigbosshorse: belongs to the GarrantyDecrypt family, because the suffix of encrypted files will be modified to chch and become keywords. The ransomware virus family mainly cracked remote desktop passwords through brute force, and then manually transmitted the virus.
l harma: Same as admin@sectex.net. The difference is that the file suffix is changed to harma
Top 10 ransomware keywords for November 2019
360 Ransomware decryption tool
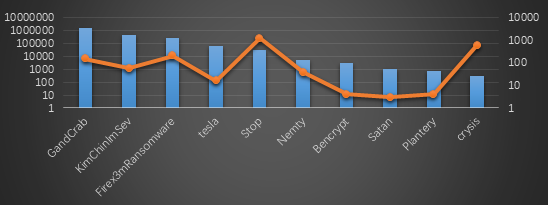
From the statistics of the decryption masters this month, GandCrab ransomware was the largest decryption this month, followed by KimChinImSev; the highest number of users who used decryption tool to decrypt files was still the equipment of the Stop family, followed by Crysis.
Decryption situation of decryption tools in November 2019
Learn more about 360 Total Security