Recently, there has been a phishing email for WordPress users. The content of the email is to inform the users that their database needs to be updated, as shown in the figure below:
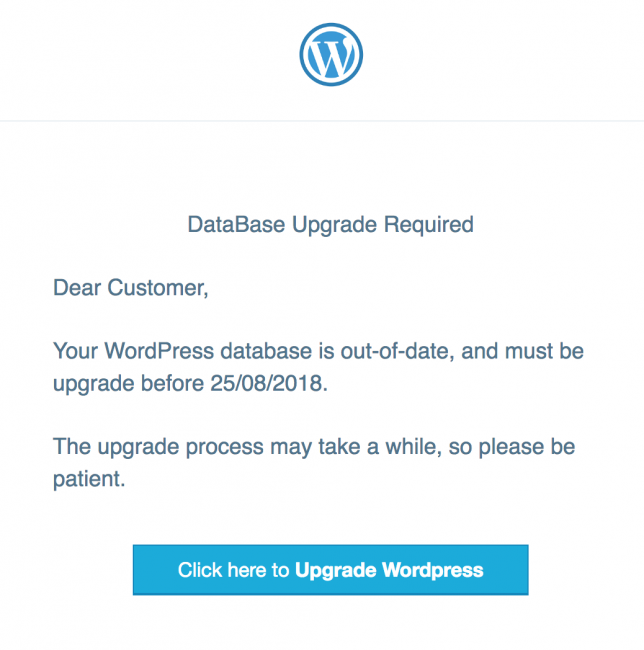
Although the email is similar to a legitimate WordPress update, there are still a number of vulnerabilities: the content contains typos and the message delivery method is older. The deadlines marked in the emails are also suspicious. WordPress officials have previously defined deadlines based on effective explanations, thus, such emails are also difficult to convince service providers. The bigger flaw is that phishing attackers even send timestamps with European formats to the users in the United States.
The footer of the email mimics the habit of Automattic (the parent company of WordPress.com, Jetpack, WooCommerce), but the link also accesses to a phishing page on another hacked website (also located at /so/subdirectory).
If the user clicks the “Update” button, the fake WordPress login page will be opened in preparation for collecting credentials. The page was created on a hacked but legitimate website. After entering the credentials and clicking the “Login” button, the web page will ask for the address and username of the website, but this behavior does not make sense during normal login. Click the “Upgrade WordPress Database” button to complete the final step of the attack, and then the victim’s credentials and website address will be sent to the attacker.
Even if the user web app is up-to-date and fully patched, if the victim provides the hacker with credentials, the hacker can still break in. Phishing attacks against common CMS networks often attempt to trick webmasters into opening web pages that resemble standard login pages and enter their credentials there without having to verify the address of the page.
In the above case, an attacker uses e-mail as a delivery mechanism to send their phishing email activity on an attacked website and collect credentials from other WordPress users. Once an attacker gains credentials for the site through this activity, they can upload backdoors, disrupt the content of the site, or use the site to provide malware. This may cause the victim to blacklist and affect the traffic and reputation of their website.
Reminder
We would like to recommend our users that they can try to follow the following simple rules to avoid the risk of phishing emails:
NEVER trust an email asking you to perform an action that you didn’t request—especially if you haven’t received such an email before.
* Verify that the sender matches the content in the email
* Check the content for spelling errors or incorrect formatting
* Check the URL to find a legal domain name








