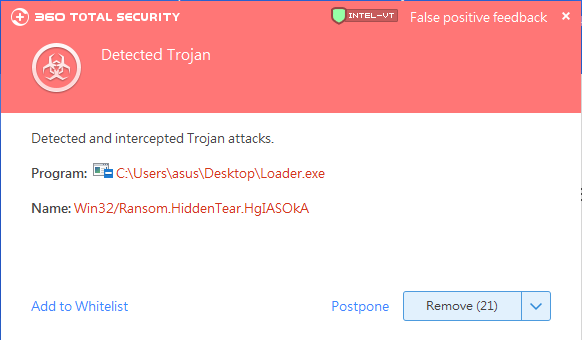
Recently, there have been many incidents of ransomware attacks. Once users are infected by ransomware, it is almost impossible to decrypt it by technical means that users can only be forced to abandon data or pay ransom to solve. Therefore, unlike other virus Trojans, the “pre-defense strategy” is different from the “after-the-fact killing strategy”.
Today, we would like to make a brief summary of the intrusion methods used by the popular ransomware on the Internet, and hope that users can take precautions.
Step 1
With the transfer of the target of ransomware, the spreading method is also changing. In the early days when ordinary users were the main target of ransomware, the spreading way of ransomware was similar to traditional Trojan virus, which mainly used phishing emails, instant messaging (IM) and drive by downloads to spread. Although these kinds of spreading methods have a high degree of automation and a large range of influence, the corresponding pertinence is low. Besides, most ordinary users choose to directly discard the encrypted data because of the low importance of data, which leads the low success rate to ransomware.
In the past two years, the ransomware has turned to more targeted attacks on various servers. Therefore, the original mode of spreading is no longer applicable to the attacks against servers. Correspondingly, RDP weak password cracking has become the main mode of intrusion.
Hackers who use this method to invade would firstly use network tools to perform an indiscriminate scan on the Internet to find servers with available ports exposed on the Internet. Once found, the dictionary tool can be used to crack service login password corresponding to the port. If the login password set by the administrator is not strong enough, the hacker may easily crack and successfully log-in in a short time.
In the process of handling user feedback, 360 Security Center captured cases in which hackers used Intercepter-NG, NetworkShare and other network scanning tools to conduct initial network scanning attacks.
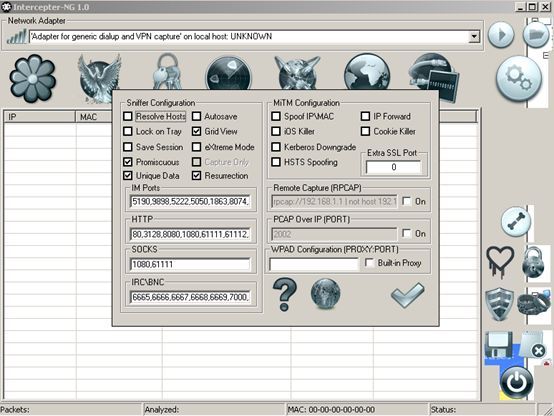
In a feedback case, 360 Security Center received a request from a technology company, saying that multiple servers of its company received ransomware attacks at the same time, unable to operate normally, and the data loss was serious.
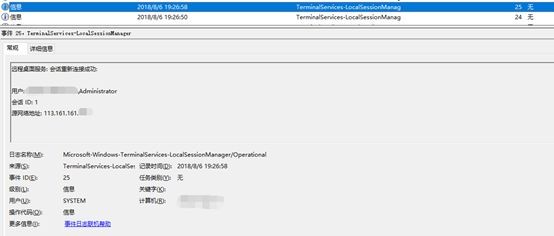
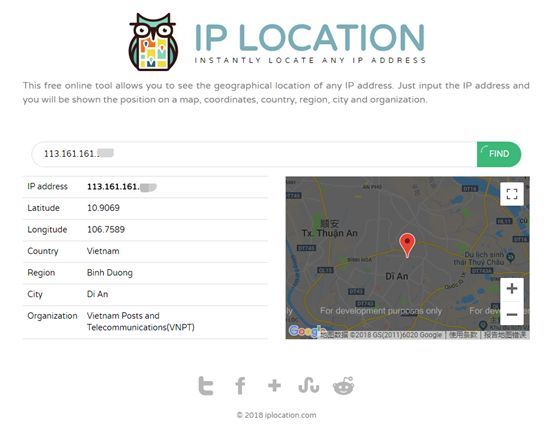
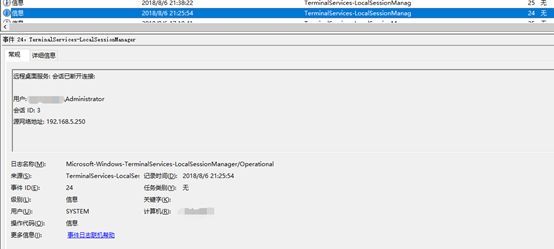
After our analysis, the company’s server was originally exposed to the Internet that directly has a financial server. It is because the server opened the remote desktop server, and set a weak login password, resulting in an external suspicious IP (According to public data query, probably from Vietnam) cracked the login password and successfully logged into the administrator account (Administrator):
Step 2
After completing the above steps, the intruder will not stop at the current results. Instead, the machine which is currently logged in will be used as a springboard to further invade other machines in the same LAN. In this step, hackers mainly use three means:
Firstly, the various network scanning tools we mentioned in the first step are equally applicable to the LAN. Therefore, in this step, the tool mentioned above can also be used for secondary intrusion scanning in the local area network.
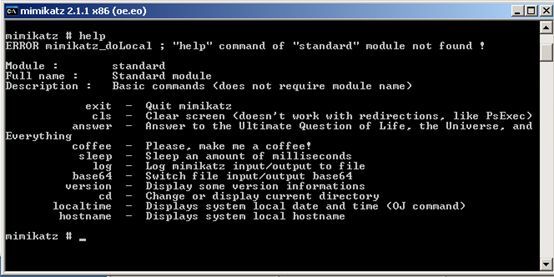
Secondly, based on the past cases, 360 Security Center has repeatedly captured various types of password sniffing tools such as mimikatz and WebBrowserPassView in such attacks. Such tools are mainly used to obtain passwords stored locally on the machine, thereby greatly increasing the success rate of other machines invading the intranet.
Thirdly, there have been many cases of exploiting vulnerabilities for network intrusion and launching ransomware recently such as the previously discovered JBOSS exploits (CVE-2017-12149, CVE-2010-0738), WebLogic exploits (CVE) -2017-10271), Tomcat exploits, etc.
In addition,users need to pay more attention to recent outbreak of ransomware. After analysis, this event is the latest variant of the GlobeImposter family, Ox4444. This variant has almost no difference in the core function code from the previous variants of this family.
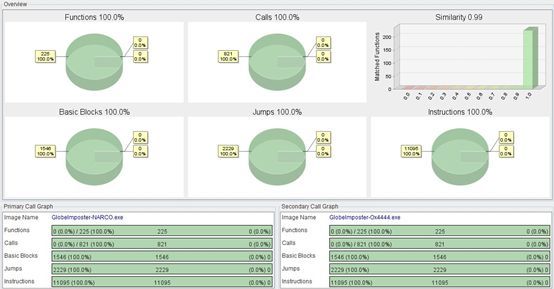
However, by analyzing the user system, we found that the core of this variant is not the ransomware itself, but the way of intrusion. In the spread of this variant, the toolkit for ShadowBrokers exploit the vulnerability was used for the first time.
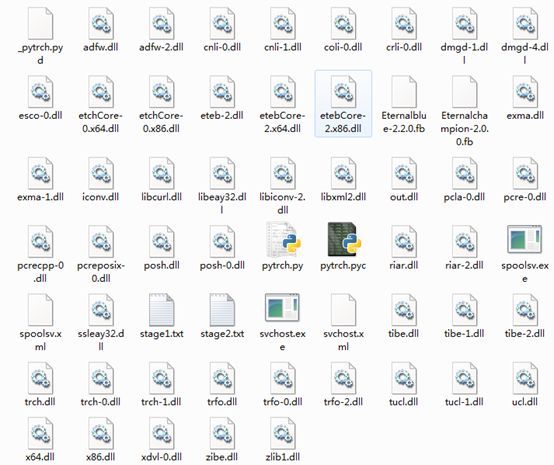
It can be seen that although the vulnerability has been fixed, hackers will not let go of any possible successful intrusion.
In the feedback case mentioned above, when we continue to analyze other machines, we find that most of these machines are not directly connected to the Internet, and the source of invading these internal servers is exactly the external suspicious IP:
Step 3
Whether it is an external direct invasion or a second invasion through a springboard, after the invasion, the core purpose of the hacker is still to encrypt the data in the server system. Before that, we must first make a simple “clean up” of the system to pave the way for the virus.
At this point, various process management tools or Rootkit tools come in handy. Based on past cases, ProcessHacker has become the most popular tool due to its powerful features. Hackers often use it in conjunction with the acquired system administrator privileges to end the process of security software or other backup software, and sometimes to clean up the database service, so that the virus cannot encrypt data files:
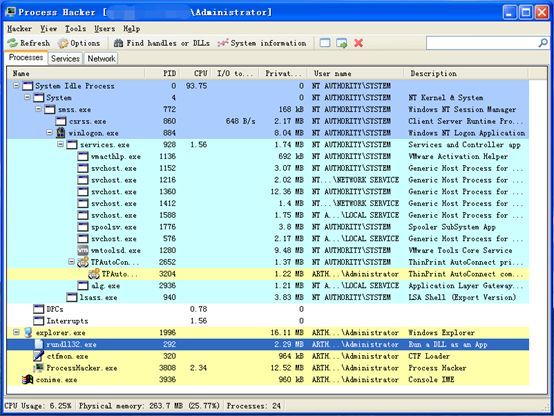
Step 4
In the end, all the preliminary work is completed, at this time the hacker already has the system administrator privileges, and there is no longer any security and backup software in the system to interfere with the virus. At this time, the hacker can directly send the ransomware to the system for encryption and extortion.
In addition, some hackers will also launch remote control Trojans or backdoors to facilitate subsequent logins to achieve long-term control of the compromised machines.
In summary, a complete set of intrusion poisoning processes is that the hacker can successfully invade a machine exposed on the Internet. If this step fails, the hacker will have nothing to do, but if this step is successful, the hacker will be almost successful as well. If the machines on the intranet also have weak passwords or vulnerabilities, even if these machines are not directly exposed to the Internet, they will be hacked by hackers in the presence of intranet springboards, and sometimes even inside. Sometime the network machine repeatedly infects each other.
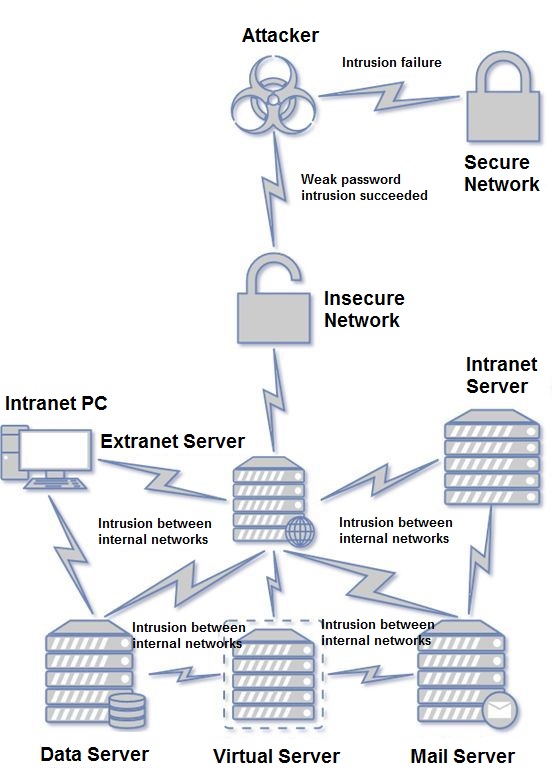
Conclusion and Reminder
It can be seen from the above summary that the hacker has obtained the administrator authority of the server in the first two steps. It can be seen that the latter two steps are completely inoperative, so the focus of the current ransomware prevention must be placed on preventing hackers from invading. The 360 Security Center gives the following eight suggestions:
1. Avoid using too simple passwords in the server. The login password should be a combination of uppercase and lowercase letters, numbers, and special symbols, and keep the password of sufficient length. Also, add a security policy that limits the number of failed logins and periodically change the login password.
2. Do not use the same or similar login password for multiple machines.
3. Use isolated backup to restore important information on a regular basis. Users should pay more attention to “isolated backup” since sometimes backup server are encrypted together in the same network.
4. Patch system vulnerabilities in a timely manner, and don’t ignore security patches for common services.
5. Turn off non-essential services and ports such as 135, 139, 445, 3389 and other high-risk ports.
6. Strictly control the permissions of the shared folder, and take the cloud collaboration as much as possible.
7. Improve security awareness, do not click on unfamiliar links, email attachments from unknown sources, files sent by strangers through instant messaging software. Perform security scans before clicking or running, and download and install software from secure and trusted channels.
8. Install 360 Total Security and ensure that security monitoring is up and running normally, and update the software in time.
Learn more about 360 Total Security