The spread of ransomware has brought serious security threats to businesses and individuals. 360 Security Center conducts comprehensive monitoring and defense against ransomware. Four more popular ransomware families, SpartCrypt, BRCrypt, Montserrtat and Zeppelin, were added this month.
360 Decryption Tool added decryption of MZRevenge and TRSomware family in December 2019.
Analysis of infection data
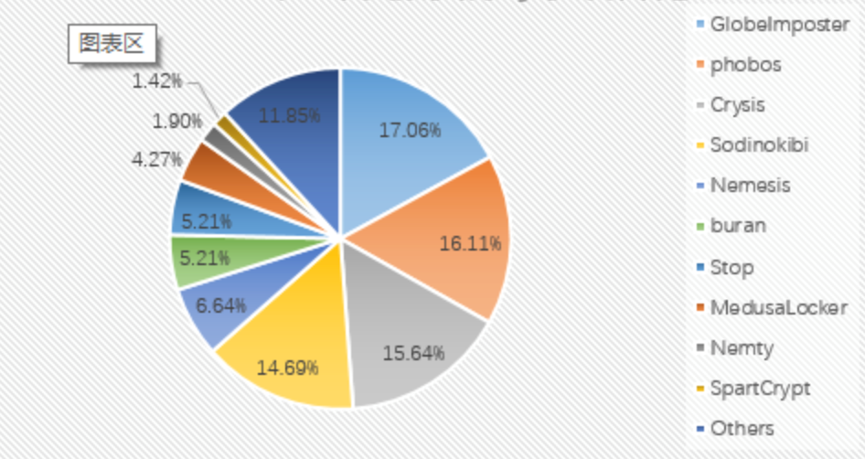
Analysis of the percentage of ransomware families this month: The GlobeImposter family accounted for 17.06%, ranking first; followed by the phobos family with 16.11%; the Crysis family ranked third with 15.64%. Compared with the data in November, the Stop family’s share has changed most significantly, from 15.18% in November to 5.21% this month.
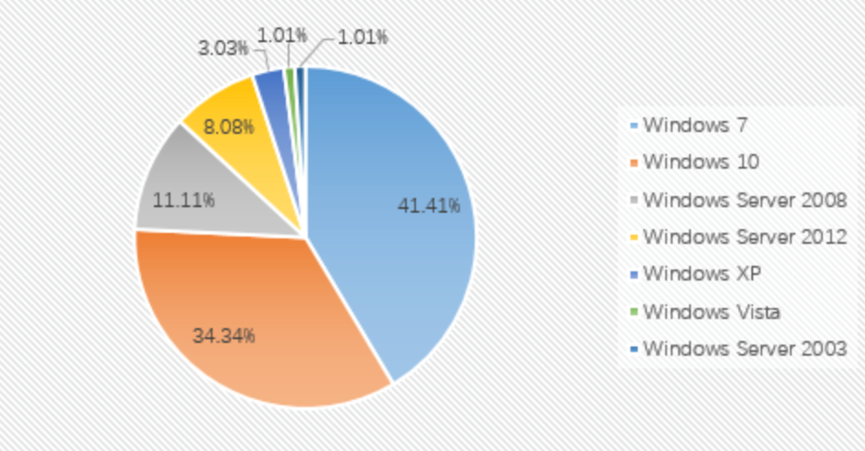
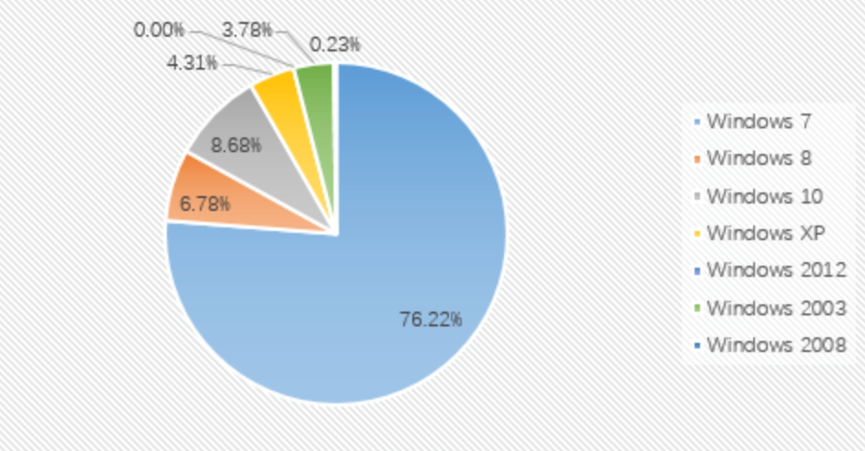
From the proportion of infected systems: Windows 7, Windows 10, and Windows Server 2008 are still the top three systems this month. Among them, the proportion of Windows 7 rose significantly this month. From 28.94% in November to 41.14% this month.
The proportion of desktop systems and server systems in the infected systems in December shows that the main attacked systems this month are still desktop systems. Compared with the statistics in November, the proportion of desktop systems rose from 58% to 79%. The main fluctuation comes from the increase in the proportion of Windows 7 systems.
Maze ransomware family
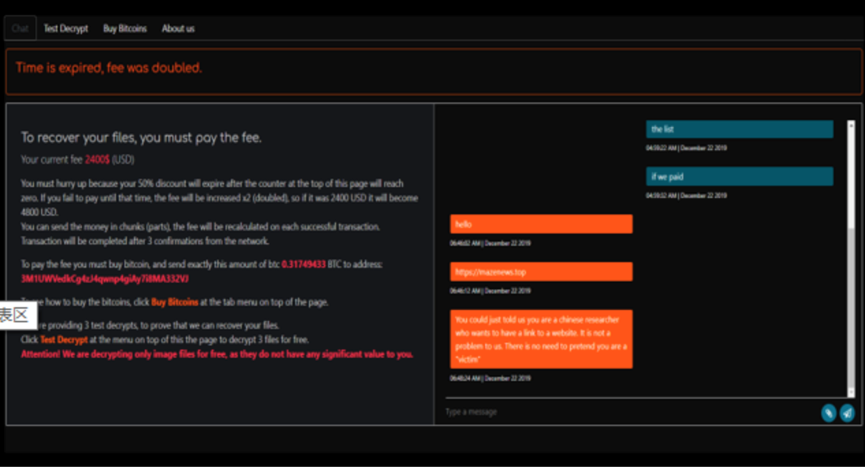
Maze ransomware is also known as “maze ransomware virus” or “chacha ransomware virus”, and it was first transmitted in China in June 2019. The ransomware was revealed this month and threatened to disclose confidential data to victims who did not pay the ransom, forcing users to pay the ransom for profit. The victims who have been released by the data include: Southwrie (120GB), DV-GROUP (7GB), Fratelli Beretta (3GB), Canadian Insurance Company (1.5GB), Pensacola City (2GB) and other victim groups.
360 Security Center detected that the virus was mainly transmitted through webpages when it first entered China in June. According to the current domestic feedback of infection cases, it will also be transmitted through remote desktop blasting and poisoning. The virus asks the average victim for $ 2,400 worth of bitcoin (for targeted attacks, ransoms cost hundreds of thousands or even millions of dollars).
MZRevenge ransomware family
360 Security Center detected a new type of ransomware, MZRevenge, which uses a symmetric encryption algorithm modified by the author. Each file has the same encryption key. Then use the AES256 symmetric encryption algorithm key hard-coded in the virus to encrypt the key of the encrypted file. Asymmetric encryption algorithms are not used in the entire encryption process, which leads to the use of passwords hard-coded in viruses to obtain global file encryption keys from ransomware prompt files for data recovery.
The users of MZRevenge ransomware can use the 360 Decryption Tool to decrypt the encrypted files.
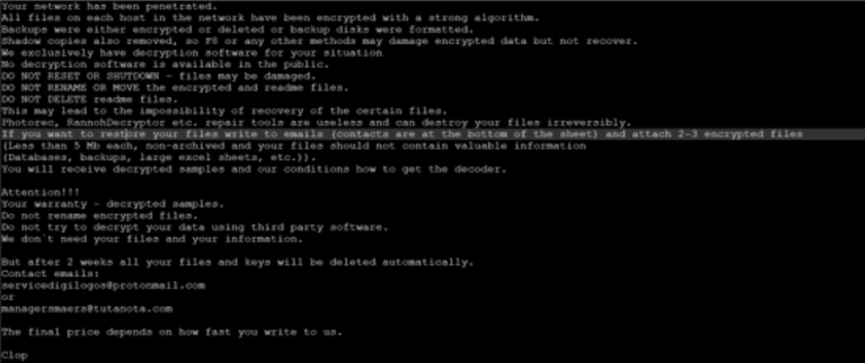
Cl0p ransomware family
Cl0p (also known as Clop) ransomware is a variant of the CryptoMix ransomware family, which began to appear in February 2019. This time, it is the latest variant that has been distributed in China. This variant has several optimizations compared to the previous version. For example, it will preferentially encrypt 2019 files, use the RC4 algorithm to increase the encryption speed, and use a custom algorithm to generate random numbers. And in terms of ending processes, the number of ending process lists is as high as 663. More importantly, the ransomware spreader will target specific enterprises to infiltrate the attack. The virus implanted by each attacked company is customized. You can also see the ransomware prompts left on the victim’s machine. However, the user id information is not included in the ransomware (the attacker knows every company they attack). In terms of ransom, the asking price of the ransomware is more than one million US dollars, which has a huge impact on enterprises.
Buran ransomware family
Buran ransomware was primarily transmitted by spam delivery in the early days, and new variants of the ransomware virus have been detected. The attack method used in this variant mainly uses manual brute force after violently cracking the remote desktop login password. At the same time, it also uses the compromised machine as a springboard to attack other machines on the intranet, resulting in batches of intranet machines being encrypted. The ransomware not only clears RDP connection records, system log records, but also disables event records, thereby hiding the source of the attack.
The ransomware currently has two variants, both of which are active: Variant 1 with modified file suffix [xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx]; Variant 2 with modified file suffix: xxx-xxx-xxx. And leave a ransom note, let users actively contact the mailbox left by the hacker to inquire about the decryption.
The following is the hacked mailbox information collected in this month:
| dresden@protonmail.com | decryptfiles@qq.com | RobSmithMba@protonmail.com |
| omg@onlinehelp.host | decryptfiles@countermail.com | zoye1596@protonmail.com |
| zeppelin_helper@tuta.io | decrypt@files.com | volscatisbi1974@protonmail.com |
| zeppelin_decrypt@xmpp.jp | decodeyourfiles@cock.li | notopen@countermail.com |
| murzik@jabber.mipt.ru | deccrypasia@yahoo.com | zandra_simone1995@protonmail.com |
| moncler@tutamail.com | deathransom@airmail.cc | noferasna1982@aol.com |
| notopen@cock.li | deadmin@420blaze.it | yoursalvations@protonmail.ch |
| noallpossible@cock.li | david-angel@sohu.com | cryptographythebest@gmail.com |
| youhaveonechance@cock.li | datarestore@iran.ir | newrecoveryrobot@pm.me |
| youcanwrite24h@airmail.cc | datarest0re@aol.com | neverdies@tutanota.com |
| you.help5@protonmail.com | cyborgyarraq@protonmail.ch | neo1312@protonmail.com |
| yeahdesync@airmail.cc | cyberdyne@foxmail.com | zeppelindecrypt@420blaze.it |
| yardimail2@aol.com | Cryptonium@cock.li | mr.obama21@protonmail.com |
| yardimail1@aol.com | nmare@cock.li | ContactReception@protonmail.com |
| winnipyh123@sj.ms | crypt@ctemplar.com | montserrat501@protonmail.com |
| WilliGarcia@protonmail.com | createhelp@protonmail.com | montserrat501@airmail.cc |
| nyton@cock.li | cosmecollings@aol.com | moneymaker2@india.com |
| volcano666@tutanota.de | morf56@meta.ua | zanzarah2019@tutanota.com |
| volcano666@cock.li | pain@cock.lu | merosadecryption@gmail.com |
| jones0helper@cock.li | collyhuwkmac@tutanota.com | MerlinWebster@aol.com |
| loplup@tutanota.com | cockroach@rape.lol | support@anonymous-service.cc |
| mailnitrom@airmail.cc | cockroach@cock.lu | mailnitrom@tutanota.com |
| unlock@royalmail.su | chitoz@protonmail.com | mailnitrom@protonmail.ch |
| unlock@graylegion.su | china.hepler@aol.com | Unlockme501@protonmail.ch |
| unblock@badfail.info | china.helpen@ao1.com | luciferenc@tutanota.com |
| tryopen@cock.li | burkbertie@musicradle.com | lordcracker@protonmail.com |
| foxbit@tutanota.com | locust@cock.li | unpedavol1972@protonmail.com |
| thunderhelp@airmail.cc | buratino@firemail.cc | buratin@torbox3uiot6wchz.onion |
| theonlyoption@qq.com | loplup@cock.li | buricoume1976@protonmail.com |
| theone@safetyjabber.com | Buddy@criptext.com | kippbrundell@magte.ch |
| tealjanos@aol.com | BTC@decoding.biz | kingsleygovan@krnas.com |
| sydney.fish@aol.com | btc2018@qq.com | keysfordecryption@jabb3r.org |
| sverdlink@aol.com | bron_lynn@aol.com | keysfordecryption@airmail.cc |
| supportrest1@cock.li | Blackmax@tutanota.com | kermy.stapleton@vuzup.com |
| supportdecrypt@firemail.cc | bitlocker@foxmail.com | kensgilbomet@protonmail.com |
| itsnotajoke@firemail.cc | BigBobRoss@protonmail.com | karrie.murphey@aol.com |
| manyfiles@aol.com | BigBobRoss@computer4u.com | jones0helper@countermail.com |
| support98@cock.li | Big8obRoss@protonmail.com | unumschooler1972@protonmail.com |
| support7164@firemail.cc | bexonvelia@aol.com | joker8881@protonmail.com |
| support4568@mail.fr | jjcryptor@cock2.li | suiren2852@protonmail.com |
| support.mbox@pm.me | back_filein@protonmail.com | bapuverge1985@protonmail.com |
| superuser111@0nl1ne.at | back_data@protonmail.com | jason.ving@tutanota.com |
| jodygomersall@aol.com | jackpot@jabber.cd | James_Langton_2019@protonmail.com |
| suiren2852@cock.li | backmyfiless@tutanota.com | backupmyfiles@protonmail.com |
| strang.shani@aol.com | backdata.company@aol.com | backcompanyfiles@protonmail.com |
| stocklock@airmail.cc | jackbtc@mail.ua | jabber-winnipyh123@sj.ms |
| stillmann.mnu@aol.com | asus2145@cock.li | jabber-theone@safetyjabber.com |
| stelskill@cock.li | asdbtc@aol.com | jabber-hellobuddy@sj.ms |
| stanley001@cock.li | asdasd333@default.rs | support@robsmithmba.com |
| sqlbackup2019@pm.me | hyena@rape.lol | isafeyourdata@protonmail.com |
| SoupMactavish@cock.li | apoyo2019@protonmail.com | ingalls.jan@inqwari.com |
| Skynet228@cock.li | apoyo2019@aol.com | info@bigbobross.website |
| hyena@cock.lu | angry_war@protonmail.ch | ImranZakhaev@protonmail.com |
| imdecrypt@aol.com | anamciveen@aol.com | sherminator.help@tutanota.com |
| seed@firemail.cc | altecpro@cock.li | iamheretohelpy0u@protonmail.com |
| SafeGman@tutanota.com | altec433@cock.li | ArcticBearSOS@protonmail.com |
| safegman@protonmail.com | altec1167@cock.li | Skynet1488@protonmail.com |
| SafeGman@firemail.cc | alleen.cowthwaite@aol.com | human_mystery@aol.com |
| rsa2048@cock.li | aliradada@tutanota.com | howdecript@tutanota.com |
| Fata54@cock.li | aliradada@protonmail.com | recoverydbservice@protonmail.com |
| file1m@yandex.com | aksdkja0sdp@ctemplar.com | recoverydata52@protonmail.com |
| restoringbackup@airmail.cc | Agent.DMR@protonmail.com | detwavuka1973@protonmail.com |
| restorehelp@qq.com | Agent.DMR@aol.com | heronpiston@xmpp.jp |
| reroman4@gmail.com | admincrypt@protonmail.com | heronpiston@ctemplar.com |
| requests2@memeware.net | admin@spacedatas.com | helpyou@countermail.com |
| recoveryhelp@airmail.cc | admin@sectex.net | helpservis@horsefucker.org |
| hinkle.s@aol.com | admin@secet.net.bot | helprestore@firemail.cc |
| recoverydata54@cock.li | admin@secet.bot | helpdesk_mz@aol.com |
| horsesert@xmpp.jp | admin@sctex.net | recovery94@protonmail.com |
| hellobuddy@sj.ms | admin@datastex.club | healermed@protonmail.ch |
| recoverdata@cock.lu | 5ss5c@mail.ru | harmahelp73@gmx.de |
| GodSaveYou@tuta.io | 4josefina@keemail.me | Hamlampampom@cock.li |
| file1@techie.com | gnus@nigge.rs | grusha2281@protonmail.com |
| Rans0me@protonmail.com | 1btc@qbmail.biz | ReadME-Unlockme501@protonmail.ch |
| protected@firemail.cc | everbe@airmail.cc | GodSaveMe@tutamail.com |
| prndssdnrp@mail.fr | estelldstva@aol.com | 1btcpayment@protonmail.com |
| prndssdnrp@foxmail.com | geerban@email.tg | elisa_abbott1983@protonmail.com |
| prnassdnrp@maill.fr | gaudrea@aol.com | getdecoding@protonmail.com |
| Philip.BTC@protonmail.com | embrace@airmail.cc | getbackdata@qq.com |
| pc.master@aol.com | gnus@cock.li | esliperre1971@protonmail.com |
| file1@protonmail.com | elamsanjit@airmail.cc | eninteste1987@protonmail.com |
| file1n@yandex.com | duncnock@gerdye.com | Galgalgalhalk@tutanota.com |
| deliverymax@tutanota.com | dresdent@protonmail4.com | truesoft77@protonmail.com |
| file1@keemail.me | dresden@protonmail.com | fox606@protonmail.com |
| decservice@mail.ru | dontworry@tuta.io | firstmaillog@protonmail.com |
| decryptors@xmpp.is | dontworry@hitler.rocks | dharma99@protonmail.com |
| decryptmasters@firemail.cc | dontworry@cock.li | decyourdata@protonmail.com |
| howdecript@cock.li | donshmon@cock.li | panda.in.prada@tutanota.com |
| divinebackup@tuta.io | evillocker@cock.li | panda.in.prada@outlook.com |
| divine@cock.lu | evillock@cock.li | returnmaster@aaathats3as.com |
| fhmjfjf@default.rs | everest@airmail.cc | rdpconnect@protonmail |
System security protection data analysis
By comparing the data from November and December 2019, we found that in terms of the proportion of attacked systems, the remote desktop weak password attack suffered by Windows 7 increased from 63.18% in November to 76.22% this month, an increase of 13.04%, Which also caused a significant increase in the proportion of desktop systems being attacked this month.
An analysis of the trend of weak password attacks in December 2019 found that MSSQL weak password attacks showed a downward trend overall in December. This is in line with the overall trend of the amount of machines monitored by the 360 security center, using the MSSQL attack channel to poison.
Ransomware Keywords
This data comes from the search statistics of lesuobingdu.360.cn. (Excluding WannCry, AllCry, TeslaCrypt, Satan, Kraken, Jsworm, X3m, and GandCrab families whose query volume has been greatly disturbed)
- pig865qqz: belongs to the GlobeImposter family, because the encrypted file suffix will be modified to pig865qqz and become keywords. The ransomware virus family mainly cracked remote desktop passwords by brute force, and then manually transmitted the virus.
- wecanhelp: belongs to the Nemesis ransomware family. The ransomware recently spread through brute force remote desktops. The ransomware generates a temp000000.txt file in the system, which contains the key used to decrypt the file. Generally, it will be deleted by hackers directly, but Infected users can try to retrieve the content of temp000000.txt in the following link: https://bbs.360.cn/thread-15780698-1-1.html.
- rooster865qqz: same as pig865qqz.
- bitlocker@foxmail.com: belongs to the Crysis ransomware virus family. Because files are encrypted, they will be added to admin@sectex.net and become keywords. The ransomware virus family mainly cracked remote desktop passwords by brute force, and then manually transmitted the virus.
- Readinstructions: belongs to the MedusaLocker family, because the encrypted file suffix will be modified to Readtheinstructions and become keywords. The ransomware virus family mainly cracked remote desktop passwords by brute force, and then manually transmitted the virus.
- Harma: Same as admin@sectex.net. The difference is that the file suffix is changed to harma
- Hendrix: Same as Readinstructions.
- Wiki: Same as harma.
- Sodinokibi: Sodinokibi is the name of the virus family. Because this ransomware modifies the encrypted file suffix to a random suffix, most users will hit Sodinokibi with the encrypted file suffix. The ransomware spreads through many channels. There are two main channels that are still being used. The first is the delivery of spam mailboxes and the second is the remote desktop brute force cracking.
- helper@aol.com: belongs to the GlobeImposter family. This email address is used by hackers to stay in the ransomware prompts and used to talk to hackers.
360 Decryption Tool
From the statistics of decryption masters this month, GandCrab still has the largest amount of decryption this month, followed by KimChinInSev. Among them, the highest number of users who use the decryption master to decrypt files is still the Infected device of the Stop family, followed by the Crysis family of Infected devices.
Summary
Attacks on servers are still a major direction of current ransomware. Enterprises need to strengthen their own information security management capabilities-especially weak passwords, vulnerabilities, file sharing and remote desktop management, in order to deal with the threat of ransomware Here are some suggestions for administrators:
- Multiple machines, do not use the same account and password
- The login password should be of sufficient length and complexity, and the login password should be changed regularly.
- The shared folder of important data should be set up with access control and be backed up regularly
- Regularly detect security vulnerabilities in the system and software and apply patches in a timely manner.
- Check the server regularly for abnormalities. View scope includes:
- a) Are there any new accounts
- b) Guest is enabled
- c) Is there an exception in the Windows system log
- d) Is there any abnormal interception of antivirus software?
As for the ransomware that has re-emerged this month and launched an attack on personal computers, users are advised to:
- Install security software and make sure it works properly.
- Download and install software from regular channels.
- For unfamiliar software, if it has been intercepted by antivirus software, do not add trust to continue running.
In addition, neither corporate victims nor individual victims are advised to pay ransom. Paying ransom not only encourages ransomware in disguise, but the decryption process may also bring new security risks.
Many common ransomware only encrypt the file header data. For some types of files (such as database files), you can try to recover some of the losses through data repair methods. If you have to pay the ransom, you can try to negotiate with the hacker to reduce the ransom price. At the same time, during the negotiation process, you should avoid exposing your true identity information and urgency, so as to avoid the hacker asking for the price.
Learn more about 360 Total Security