U.S. citizens will go to the polls in less than one week to make their decision on the next US President. However, who will win? The result suddenly became difficult to predict due to FBI’s revelations on Hillary Clinton’s email controversy.

On October 9th, WikiLeaks uncovered thousands of emails hacked from Hillary Clinton’s campaign chairman, John Podesta. According to these emails, Clinton has been acknowledging the connections between the governments of Saudi Arabia and Qatar and the Islamic State. These emails also indicate that these two countries have given millions of donation to the Clinton Foundation.
These revealed materials largely impact the presidential polling. However, how did WikiLeaks get these confidential emails?
Everything begins with a phishing email…
Podesta received a email on March 9th from Google as a security alert that someone was attempting to steal his password. Despite that Podesta soon forwarded this email to the IT team and got a security solution, it seemed that he still clicked the malicious link in the ‘security alarm email’ and thus had his account hacked.
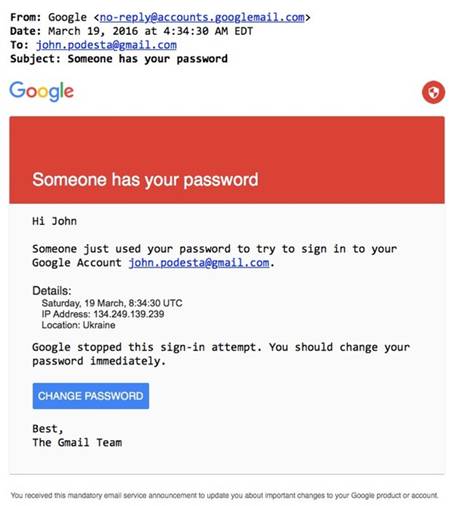
In fact, the phishing email Podesta received was a technique which tricked victims into providing his or her password to the attacker by using fake Google sign-in page and security tips. This fake Google link contains a 30-character encrypted string, including Podesta’s email address and name.
Between October 2015 and May 2016, attackers had used 213 malicious short URLs to attack Hillary’s campaign site hillaryclinton.com.
Yet, is this attack that hard to prevent?
If Podesta had enabled the two-step authentication for his Google account as a second security layer, it would be much more difficult for hackers to hack into his account.
If Podesta had been careful enough, he would have checked the URL in the email to see if it was a real Google link, so that hackers would not have the chance to steal his password.
If Podesta had not used the same password for all his social network accounts, hackers would not be able to hack into his Twitter and iCloud accounts.
Or, if Podesta had installed 360 Total Security or 360 Internet Protection browser add-on, he could have received a timely notification preventing him from entering the phishing site, so that all these tragedies would not happen.