Report Number: B6-2021-030301
Report source: 360CERT
The authors: 360CERT
Update date: 2021-03-03
0x01 event brief description
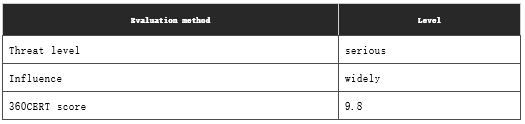
On March 3, 2021, 360CERT monitoring found that Microsoft had issued a risk notice for multiple high-risk vulnerabilities in Exchange. The vulnerabilities are numbered CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, CVE-2021-27065, Incident level: serious, incident score: 9.8.
In this regard, 360CERT recommends that users upgrade the exchange to the latest version in time. At the same time, please do a good job in asset self-inspection and prevention to avoid hacker attacks.
0x02 risk level
360CERT’s assessment of the incident is as follows
0x03 vulnerability details
CVE-2021-26855: Server request forgery vulnerability
Exchange server-side request forgery (SSRF) vulnerability, an attacker exploiting this vulnerability can send arbitrary HTTP requests and authenticate through Exchange Server.
CVE-2021-26857: serialization vulnerability
Exchange deserialization vulnerability, this vulnerability requires administrator privileges. An attacker who exploits this vulnerability can run code as SYSTEM on the Exchange server.
CVE-2021-26858/CVE-2021-27065: Arbitrary file writing vulnerability
Arbitrary file writing vulnerability after authentication in Exchange. After the attacker authenticates through the Exchange server, he can use this vulnerability to write files to any path on the server. This vulnerability can be combined with the CVE-2021-26855 SSRF vulnerability for combined attacks.
0x04 affect version
– microsoft:exchange: 2013/2016/2019/2010
0x05 repair suggestion
General repair recommendations
Microsoft has released relevant security updates, users can follow the link below to upgrade:
CVE-2021-26855: https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-26855
CVE-2021-26857: https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-26855
CVE-2021-26858: https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-26855
CVE-2021-27065: https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-26855
Temporary repair suggestions
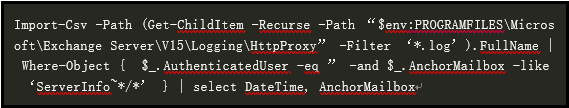
CVE-2021-26855:
It can be detected through the following Exchange HttpProxy logs:
%PROGRAMFILES%\Microsoft\Exchange Server\V15\Logging\HttpProxy
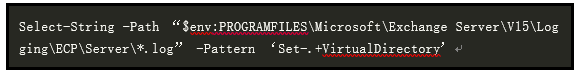
Through the following Powershell, you can directly perform log detection and check whether it is under attack:
If an intrusion is detected, the following directory can be used to obtain what activities the attacker took:
%PROGRAMFILES%\Microsoft\Exchange Server\V15\Logging
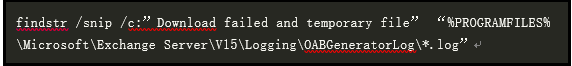
CVE-2021-26858:
Log directory: C:\ProgramFiles\Microsoft\ExchangeServer\V15\Logging\OABGeneratorLog
You can use the following command to quickly browse and check whether it is under attack:
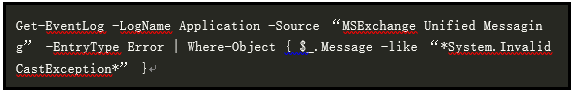
CVE-2021-26857:
This vulnerability alone is more difficult to exploit. The following commands can be used to detect log entries and check whether they are under attack.
CVE-2021-27065:
Use the following powershell commands to perform log detection and check whether it has been attacked:
0x06 timeline
2021-03-02 Microsoft releases vulnerability report
2021-03-03 360CERT release notice
0x07 reference link
1、 HAFNIUM targeting Exchange Servers with 0-day exploits
https://www.microsoft.com/security/blog/2021/03/02/hafnium-targeting-exchange-servers/
Learn more about 360 Total Security