1. Background
Recently, 360 Security Center received feedback from users regarding a malware infection. After installing an application called One System Care, victims’ computers will be infected by CryptoMiner, and the DNS settings will be altered to display ads. It updates itself by creating a PowerShell script and hides itself in system schedule tasks. This malware will start mining digital currencies on victims’ computers. 360 Total Security was the first to block this malware and millions of computers have been rescued.
2. Analysis
Behavior:
1. Create a PowerShell script in system schedule tasks.
2. Run the malware at scheduled time.
3. Executed malware will download its mining application from its update server.
4. Start mining digital currencies.
5. Even if the malware is deleted, it can always be re-created as long as the scheduled task that runs the malicious PowerShell script remains undeleted.
Characteristic:
1. Disguise itself with an appearance of legit software with digital signature.
2. Use PowerShell script to avoid antivirus detection.
3. Decrypt Downloaded file and load API dynamically to avoid static virus scan.
4. Encrypt C&C protocols to avoid interception by firewall.
5. Alter system DNS settings to hijack browser traffic for displaying advertisement.
Detail:
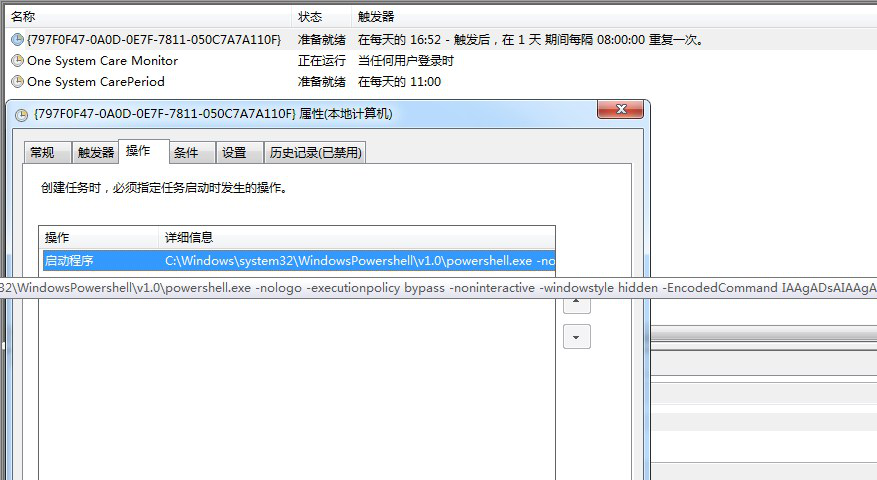
After installing One System Care, a PowerShell script was created in system schedule tasks. The script is encrypted with base64 encoding. The decoded code is as below:

The script checks a pre-configured URL regularly, malware writers can change the URL to a malware download link to trigger the mining process. After downloading and running, this malware uploads victims’ information to its control server and begins mining.
Malware’s feedback servers:
legco.info/u/
ough.info/u/
heato.info/u/
yelts.net/u/
deris.info/u/
big4u.org/u/
listcool.net/u/
listcool.info/u/
monoset.info/u/
Download links of archived and encrypted malware files:
http://xxx.info/win_setup.dat
http://xxx.info/win_setup.dat
http://xxx.info/win_setup.dat
http://xxx.info/win_setup.dat
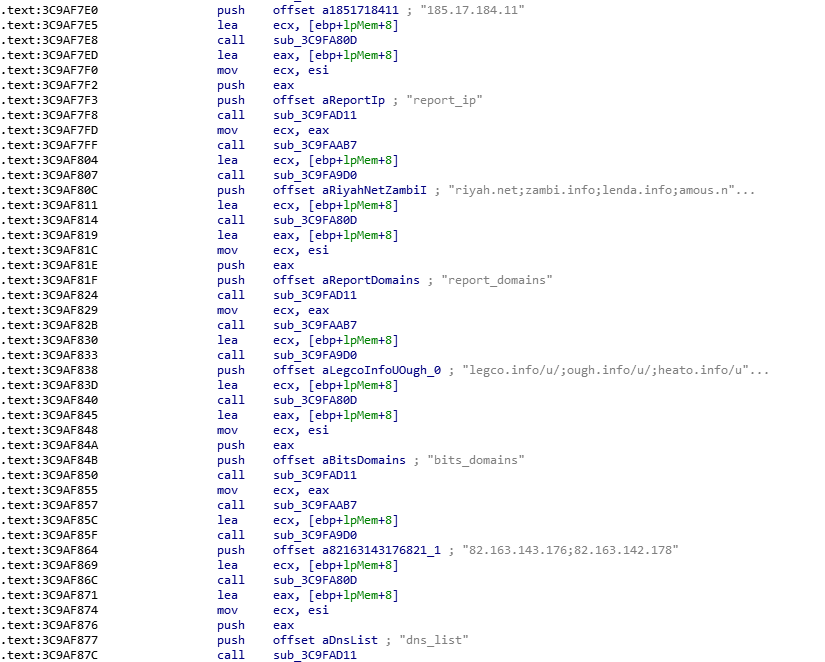
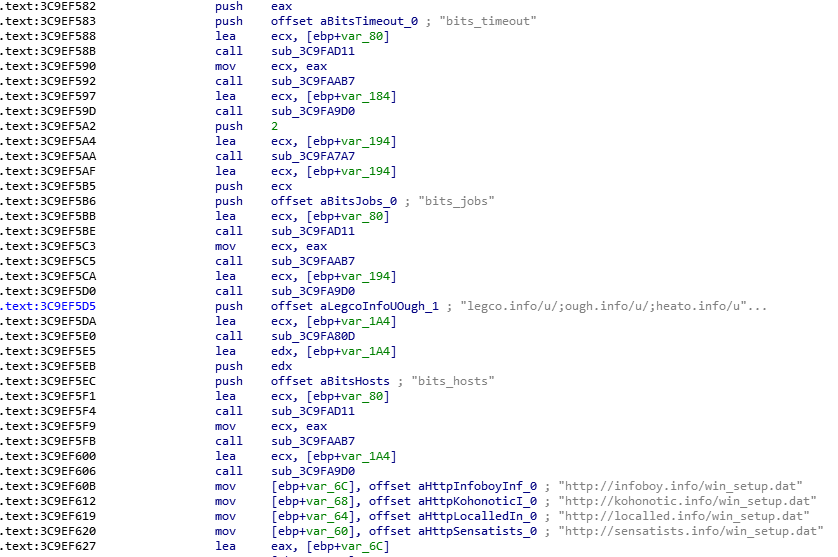
Upload computer information
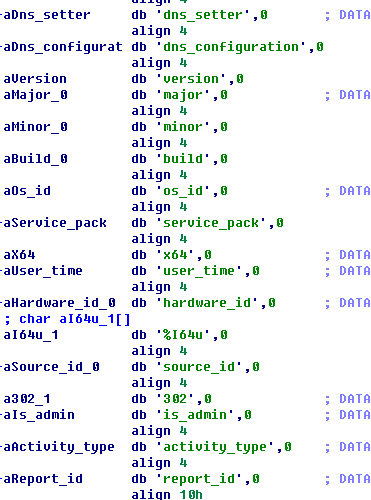
Alter DNS settings
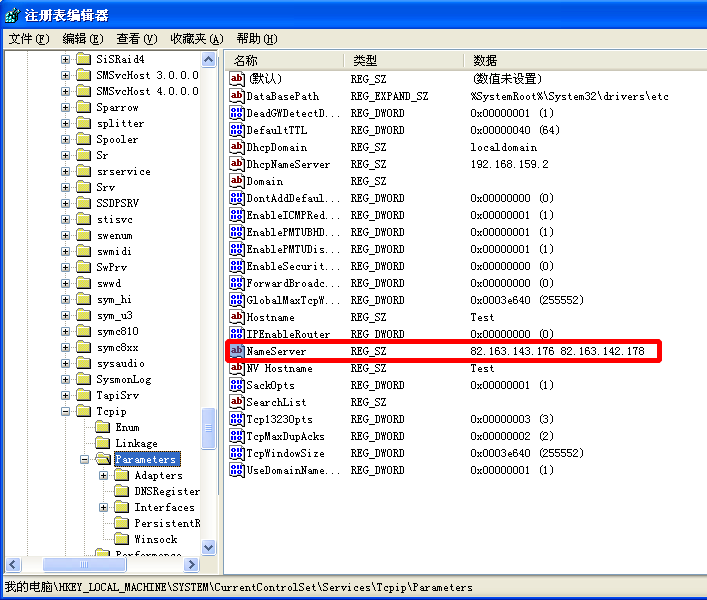
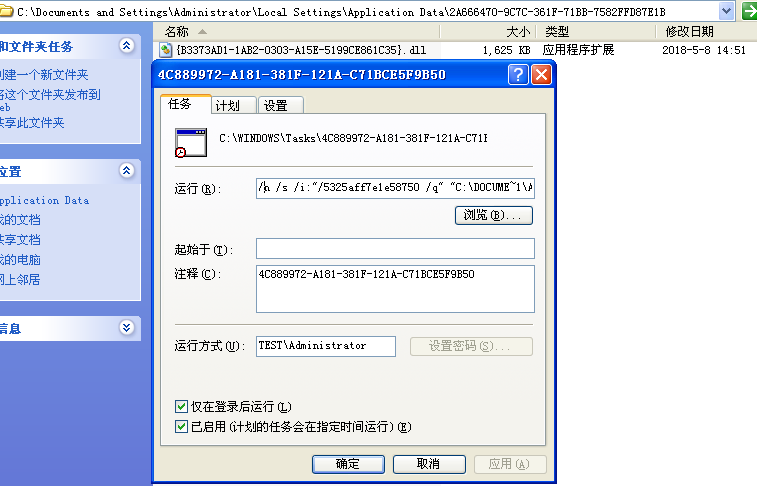
Malware downloads mining application and adds a schedule task to start itself during bootup
C:\WINDOWS\system32\regsvr32.exe /n /s /i:”/5325aff7e1e58750/q” “C:\DOCUME~1\ADMINI~1\LOCALS~1\APPLIC~1\2A6664~1\{B3373~1.DLL”
First, upload victims’ computer information.
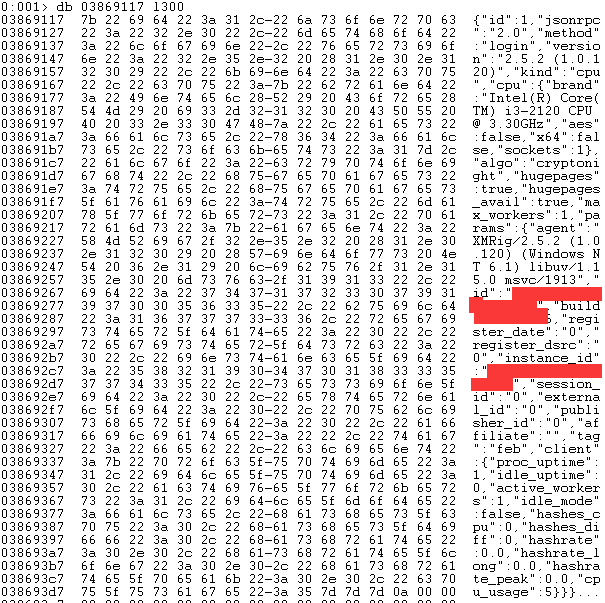
Then, the server can dispatch mining command based on victims’ hardware configurations.
The mining implementation is based on Monero’s open source code.
Mining Pool:
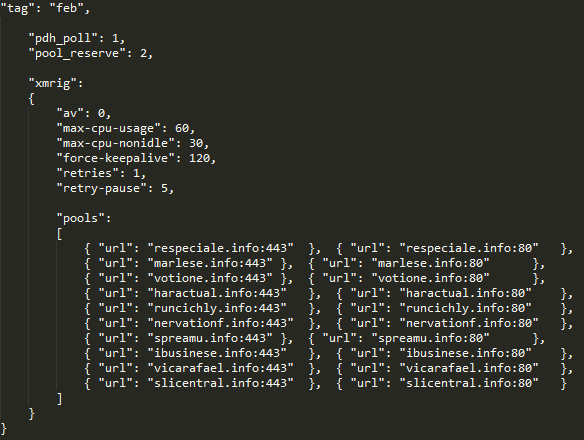
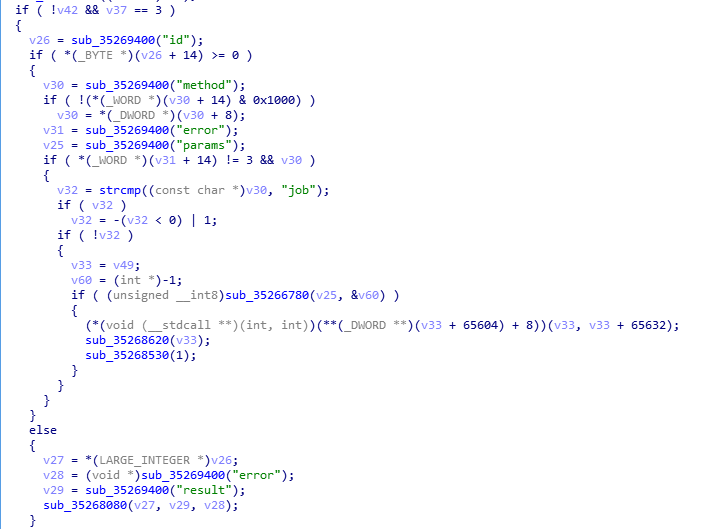
Communication protocol is encrypted. The decrypted content is as below:
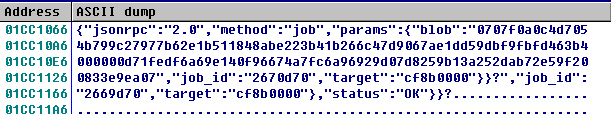

3. Related file hash in md5
f7a1b769973744d3e4b336651968af0d
3ab6d2ccaa01dbd1746f7032f38e9d5a
d5130df1eda5a018f041ac36149b7a9f
4. Reminder
Recently, we have found that a lot of CryptoMiner malware are actively spreading in the wild. We strongly recommend users to enable antivirus software while installing new applications. Users are also recommended to run virus scan with 360 Total Security to avoid falling victim to CryptoMiner.
Learn more about 360 Total Security








