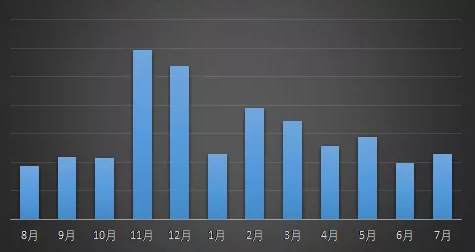
In the past July, the ransomware spread again, and 29 different family viruses continued to do evil. Among them, GlobeImposter, phobos and Stop have the most active virus family, accounting for 49.06% of the total number of the list. It is not difficult to see that with the continuous “striking” of the ransomware, the challenges faced by computer security have become more and more difficult, and it has become a paradox that directly restricts enterprise security and user experience. Therefore, the report also gives authoritative security recommendations for the prevention of ransomware for individuals and businesses.
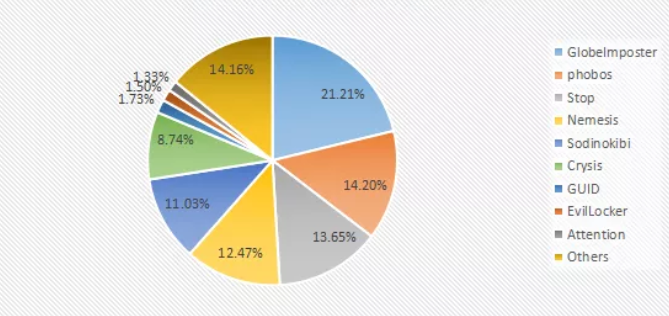
According to the report data, the trend of ransomware diversification was obvious in July, and 29 different families of ransomware emerged one after another. Among them, the GlobeImposter family won the top spot with 21.21% of the list, and the two major families of phobos and Stop together cast three dominant positions.
This situation led to an increase in the amount of anti-ransomware feedback compared to June, and the amount of Stop feedback was a rapid leap forward. Due to the customizable nature of Stop itself, the communicator can set the encrypted file suffix and encrypted file key according to his own preferences, resulting in more than 100 variants. In the middle of the month, the Stop ransomware family added a variety of suffixes such as format, bopador, masok, etc., which perfectly interpreted the virus “The Song of the Siren”, which made more users confused.
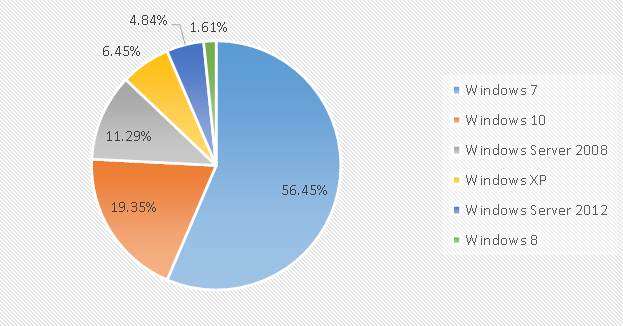
In terms of the proportion of infected systems, Windows 7, Windows 10 and Windows Server 2008 have become attack breakthroughs. Among them, the proportion of Windows 7 climbed significantly, from the 29.49% in June to 56.45% in July, becoming the “most vulnerable” in the month.
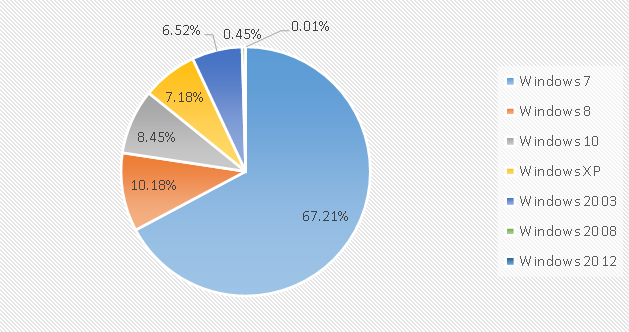
For major enterprises, server security protection is undoubtedly the most concerned issue. In the report, a comparative analysis of the server protection data in June and July 2019 found that the proportion of the attacked system did not change much, and there was a slight fluctuation in the small range. In addition, in the comparison of weak password attack data in two months, no large-scale weak password attack was found, showing a relatively stable trend.
In order to fully protect corporate and personal network security, 360 decryption tool added decryption support for the LoopCipher ransomware family in July. At the same time, from the 360 decryption tool decryption statistics, the largest amount of decryption this month is the GandCrab family, and the highest number of users using the decryption master to decrypt files is Stop and GandCrab.
Whether it is a variant of the ransomware family or an iterative upgrade of virus technology, it will undoubtedly pose a major threat to business and user security. In fact, for users who are deeply persecuted by ransomware, there is no need to deal with computers other than replace it. In order to create a safe network environment in an all-round way and safeguard the interests of many parties, combined with the extortion of the virus and the changing trend in July 2019, 360 Security Center gives the following suggestions:
- You can go to www.360totalsecurity.com to download and install 360 Total Security in time to intercept all kinds of ransomware attacks.
- Enterprise server administrators should not use the same account number and password for multiple machines, ensure login password complexity, and do regular replacement.
- The shared folder of important information should be set to access control and regular backup; regularly detect security vulnerabilities in the system and software, and patch in time.
- Individual users should download and install software from regular channels, and use various activation tools with caution; for unfamiliar software, if it has been intercepted by anti-virus software, do not add trust to continue running.
- When encountering emails sent by strangers, be cautious and try to avoid downloading attachments. If you need to download, you must first check the attachment with security software.