The spread of ransomware has brought serious security threats to businesses and individuals. 360 Security Center conducts comprehensive monitoring and defense against ransomware. This month, ransomware families such as Locked In, Ako, Geerban and HorseDeal were added.
360 Decryption Tool added decryption support for the “locked” and CHERNOLOCKER ransomware virus families in January 2020.
Analysis of infection data
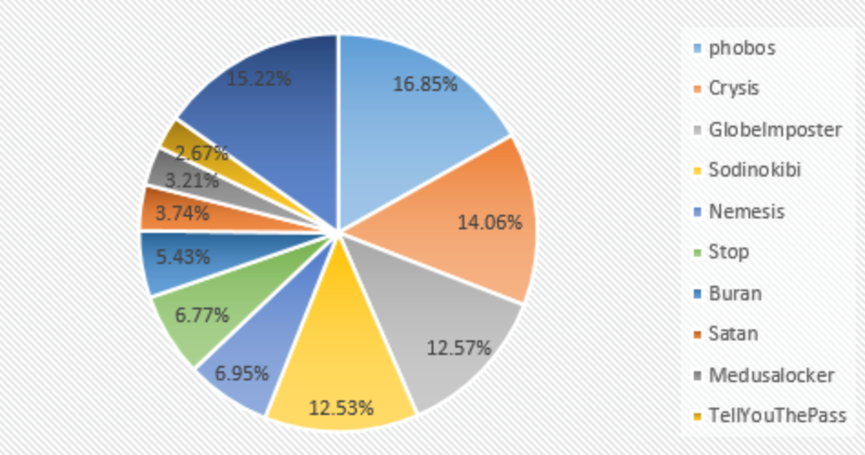
According to the analysis of anti-ransomware service data in January, the proportion of ransomware virus families: the phobs family accounted for 16.85%, ranking first; the Crysis family accounted for 14.06%; and the GlobeImposter family ranked third with 12.57%. After months of silence, the Satan ransomware virus began to spread again this month.
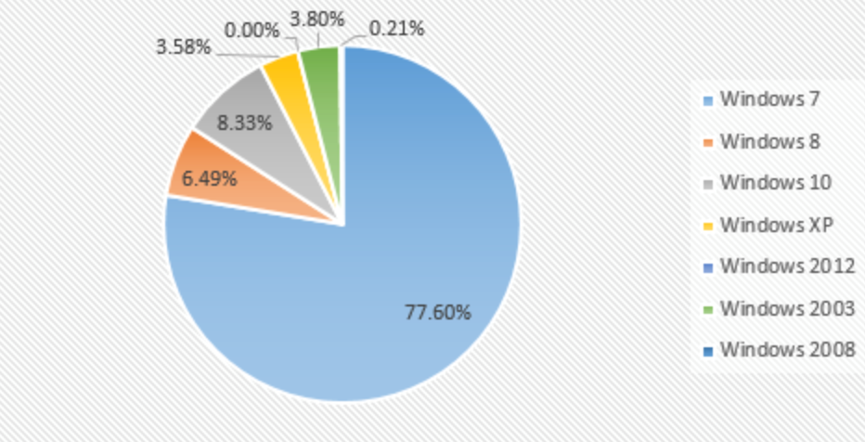
From the proportion of infected systems: Windows 7, Windows 10, and Windows 2008 are still the top three systems in this month.
The proportion of desktop systems and server systems in the infected systems in January 2020 shows that the most vulnerable systems are still desktop systems. Compared with the statistics of December 2019, there is no obvious fluctuation in the overall proportion.
“Locked” ransomware family
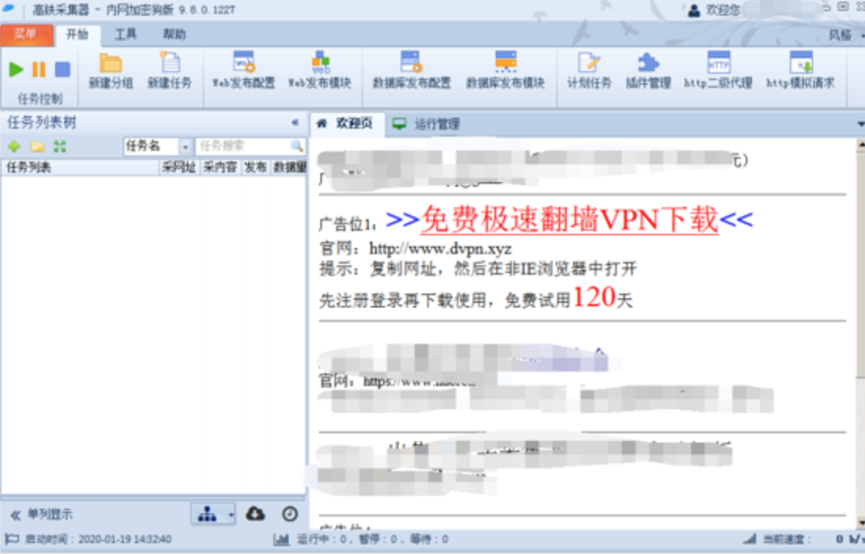
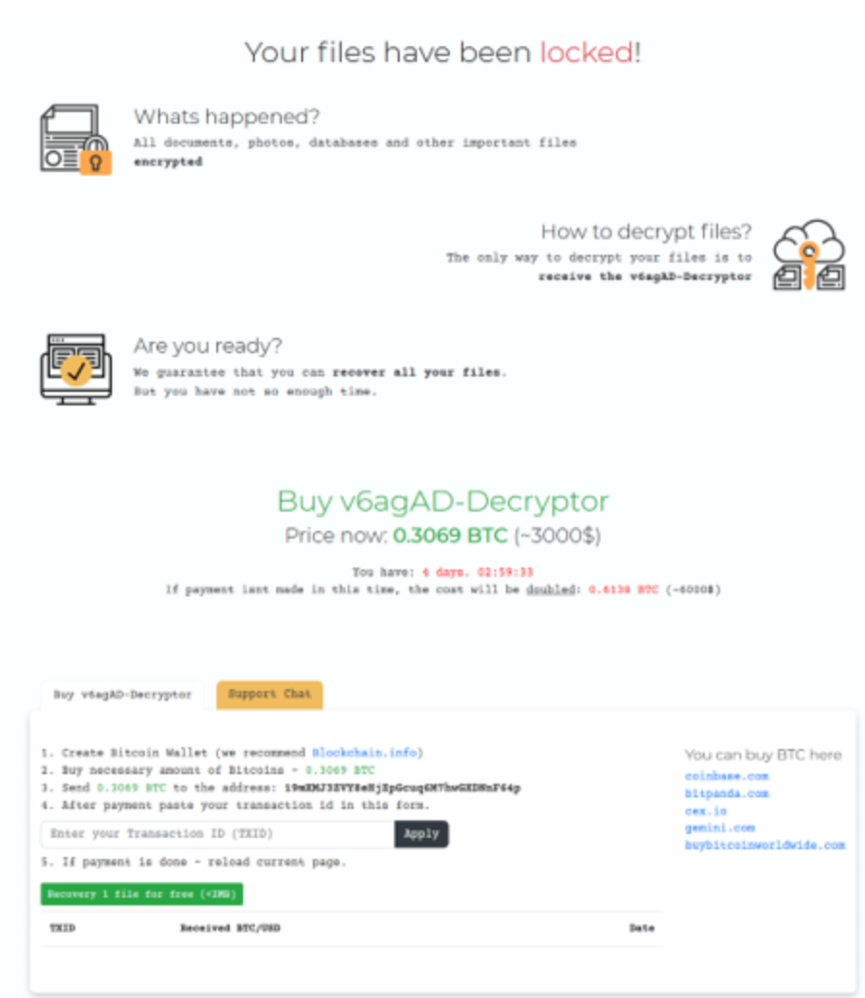
360 Security Center monitored a Chinese ransomware in mid-January 2020. The virus will add the word “locked” to the encrypted file name and generate a file lock description for each document. The virus spreader promoted on a “high-speed rail collector” software to induce users to download VPN programs with ransomware. In the process of configuring the VPN program, the author will deliberately guide users to turn off the document protection function of 360 security guards, and is equipped with related teaching videos. According to the data monitored by 360 Security Brain, the ransomware author began to plan production in November 2019, began mass spread in December 2019, and began to encrypt user files in January 2020.
The virus author also produced a very detailed decryption question and answer email, which received different decryption amounts for users with different needs, while using Bitcoin payment. 360 Security Center responded urgently as soon as the ransomware was detected and successfully cracked the ransomware. Infected users can decrypt through the “360 Decryption Tool” .
Satan ransomware family
360 Security Center has detected that the Satan ransomware virus family has returned to public sight after months of disappearance. According to the data monitored by 360 Security Center, this attack is different from previous attacks-it no longer relies on large-scale attacks, but mainly uses pan-micro vulnerabilities to attack external network machines. After the virus captures the machine, it will also use the eternal blue vulnerability, weak password blasting and other attack methods for horizontal propagation. This variant modifies the file suffix to 5ss5c, and the ransomware prompt information generated is only in Chinese and no longer English.
Ako Ransomware family
The Ako ransomware virus family has only begun to spread domestically and internationally this month. Because the ransomware code has many similarities with MedusaLocker, it was originally named MedusaReborn. But in the follow-up Ako ransomware maker publicly stated that it had nothing to do with MedusaLocker ransomware disease and was an independent ransomware virus. 360 Security Center has detected that the ransomware is currently spreading through spam and remote desktops. The encrypted file is modified to a random suffix and a file ako-readme.txt is left, asking the user for about 0.3 bitcoins.
Hacker Information Disclosure
The following is the hacked mailbox information collected in this month:
| 1024back@tuta.io | miragesity@hotmail.com | arnoldmichel2@tutanota.com |
| 5ss5c@mail.ru | cry-24hours@bigmir.net | afroditasupport@mail2tor.com |
| admin@stex777.com | newnintendoss@qq.com | don-aminado@protonmail.com |
| altec433@cock.li | no.xop@protonmail.ch | apoyo2019@protonmail.com |
| annali1984@cock.li | crypt24@protonmail.com | decrypt4data@protonmail.com |
| arzamass7@163.com | pardon1@bigmir.net | decryptmasters@firemail.cc |
| asus2145@cock.li | pardon1@protonmail.com | decryptmasters2@protonmail.ch |
| avalona.toga@aol.com | ordecrsupports@cock.li | puljaipopre1981@protonmail.com |
| averiasw@qq.com | dudaryda@protonmail.ch | billwong73@protonmail.com |
| b1tc01n@aol.com | pr0t3eam@protonmail.com | bapcocrypt@ctemplar.com |
| bajonx@blecaf.com | ptr_nyke@protonmail.ch | encryptor2020@protonmail.com |
| bajonx@iran.ir | bahebah@protonmail.com | filelocker@protonmail.ch |
| bajonx@plisr.com | qeteway@tutanota.com | charlesetta.embody@aol.com |
| bexonvelia@aol.com | rdpunlocker1@cock.li | Santagman@protonmail.com |
| billwong73@aol.com | grand@horsefucker.org | removeme2020@tutanota.com |
| billwong73@yahoo.com | remoteav@protonmail.ch | symetrikk@protonmail.com |
| bitkahelp@cock.li | foxbit@tutanota.com | help.me24@protonmail.com |
| black.block@qq.com | bitlocker@foxmail.com | skgrhk2018me@tutanota.com |
| blacklandfat@qq.com | roggers@bigmir.net | helpcore@protonmail.com |
| blackmirror@qq.com | realsapport@bigmir.net | helpfordecodevps@protonmail.com |
| Buddy@criptext.com | sivo.support@pm.me | helpforyoupc@tutanota.com |
| buydecrypt@qq.com | chian.helper@aol.com | Honeylock@protonmail.com |
| charmant@jabb.im | sumpterzoila@aol.com | info45@get-flash-microsoft-player.com |
| chinahelper@aol.com | chines34@protonmail.ch | unlocking.guarantee@aol.com |
| corposcop@airmail.cc | it24support@cock.li | viomukinam1978@protonmail.com |
| crypthelp@qq.com | webweb312@yandex.ru | datareesstore@tutanota.com |
| darkwaiderr@cock.li | westnigger@india.com | masterkry@protonmail.com |
| dataforward@bk.ru | zero2222@tutanota.com | masterkry@tutanota.com |
| decrypt@files.mn | prt.nyke@protonmail.ch | encryptor1996@protonmail.com |
| decryptfile@qq.com | wecanhelpyou@e1ude.in | clumrayjaijiu1970@aol.com |
| decryptfiles@qq.com | webweb321@tutanota.com | LordCracker@zohomail.com |
| dixolid@cock.li | kenton_hayton@aol.com | MREncptor@protonmail.com |
| fcrypt@qq.com | no.btc@protonmail.ch | 3bitcoins@protonmail.com |
| fox666@cock.li | skgrhk2018@tutanota.com | Buddy888@protonmail.com |
| gooddesh@cock.li | Cryptor6@tutanota.com | anfreesextuo1982@protonmail.com |
| Goodsant@cock.lu | Filemgr@tutanota.com | maitlandtiffaney@aol.com |
| happychoose@cock.li | payfordecrypt@qq.com | decryptyourfileshereee1@cock.li |
| happychoose2@cock.li | help@cryptmaster.info | wang.chang888@tutanota.com |
| hardlog@cock.li | no.xm@protonmail.ch | afroditateam@tutanota.com |
| help@onyon.info | sqqsdr01@keemail.me | datarecovery52@protonmail.com |
| horsefucker@tuta.io | izethroyal@aol.com | jenkins0ran@countermail.com |
| kraken@terrov.eu | manyfiles@aol.com | masterkry@tutanoto.com |
| kry.right@india.com | datarest0re@aol.com | mr.obama21@protonmail.com |
| lizethroyal@aol.com | MerlinWebster@aol.com | wangteam888@tutanota.com |
| mail@aleta.cc | LordCracker2@aol.com | online24decrypt@airmail.cc |
| name4v@keemail.me | jenkins0ran@cock.li | teroda@bigmir.net |
| nochanse@tuta.io | juli.dickonson@aol.com | King_mail7@protonmaIl.com |
| piton4800@cock.li | noallpossible@cock.li | orfhissipmay1970@protonmail.com |
| prndssdnrp@mail.fr | backdata@qbmail.biz | edinstveniy_decoder@aol.com |
| rdpcrypter@cock.li | recoverdata@cock.lu | returnmaster@aaathats3as.com |
| ret3pwn@gmail.com | buddy888@tutanota.com | fileslockers@protonmail.ch |
| sql772@aol.com | helpmanager@firemail.cc | helpservis@horsefucker.org |
| stopstorage@qq.com | charmant@firemail.cc | id-keyman@protonmail.com |
| sweetjesus@cock.li | cleta.burdett@aol.com | JasonStewem@aolonline.top |
| taargo@olszyn.com | Supportclown@elude.in | unlockransomware@protonmail.com |
System security protection data analysis
By comparing the data in December 2019 and January 2020, it is found that the proportion of each system has not changed much this month, and the top three are still Windows 7, Windows 8 and Windows 10.
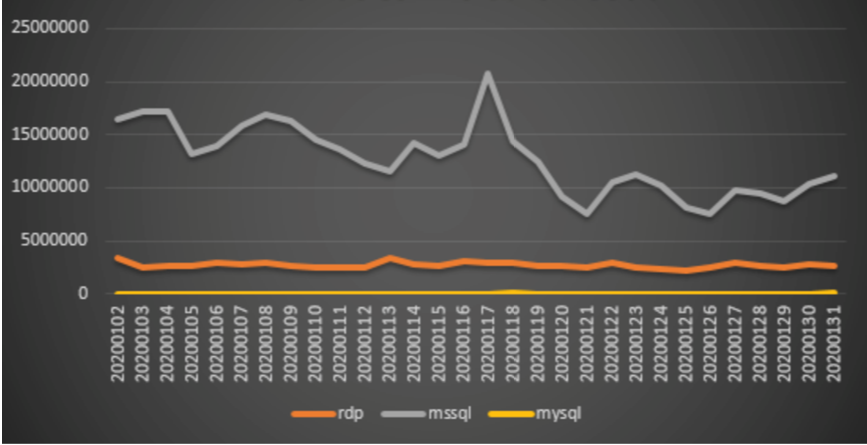
According to the analysis of the weak password attack situation in January 2020, it was found that the RDP weak password attack had a peak in mid-January 2020, and the overall trend of the attack situation of MsSQL and MySQL in this month did not fluctuate.
360 Security Center Monitor has seen a decline in the overall number of machines that have been poisoned using MsSQL attacks in this month.
Ransomware Keywords
This data comes from the search statistics of lesuobingdu.360.cn. (Excluding WannCry, AllCry, TeslaCrypt, Satan, Kraken, Jsworm, X3m and GandCrab families)
- Ako: belongs to the Ako ransomware virus family. The ransomware virus began to spread in China in January 2020. It is currently known that the ransomware virus is mainly transmitted by sending induced spam to users.
- Happychoose: Belongs to the GlobeImposter family. Because encrypted file suffixes will be modified to be Happychoose and become keywords, this ransomware virus family uses brute force to crack remote desktop passwords, and then manually spreads the virus after success. Several similar variants of the ransomware appeared this month, such as: happytwochoose, happythreechoose, happyfourchoose.
- belongs to the phobos ransomware virus family. Because the suffix of encrypted files will be modified to Devon and become the keyword, this ransomware virus family mainly cracks remote desktop passwords by brute force, and then manually spreads the virus after success.
- Readinstructions: belong to the MedusaLocker ransomware family, also known as “Medusa” ransomware. Since the encrypted file suffix will be modified to ReadInsstructions, it becomes a keyword. The ransomware virus family uses brute force to crack remote desktop passwords and then manually poisons them.
- bitlocker@foxmail.com: belongs to the Crysis ransomware virus family. Because files are encrypted, they will be added to bitlocker@foxmail.com and become keywords. The ransomware virus family mainly cracked remote desktop passwords by brute force, and then manually transmitted the virus.
- pig865qqz: Same as happychoose.
- Sodinokibi: Sodinokibi is the name of the virus family. Because this ransomware modifies the encrypted file suffix to a random suffix, most users will hit Sodinokibi with the encrypted file suffix. The ransomware spreads through many channels. There are two main channels that are still being used. The first is the delivery of spam mailboxes and the second is the remote desktop brute force cracking.
- Locked: This suffix has been used by multiple families, but the suffix that appeared this month mainly belongs to the TellYouThePass ransomware virus family. This month’s attack cases show that the ransomware mainly uses brute force to obtain database passwords for poisoning .
- decryptfiles@qq.com: Same as bitlocker@foxmail.com.
- 5ssc: belongs to the Satan ransomware virus family. Because the suffix of encrypted files will be modified to 5ss5c and become the key word, the ransomware mainly spreads through the pan-micro OA vulnerability, and also uses the eternal blue vulnerability for horizontal transmission.
360 Decryption Tool
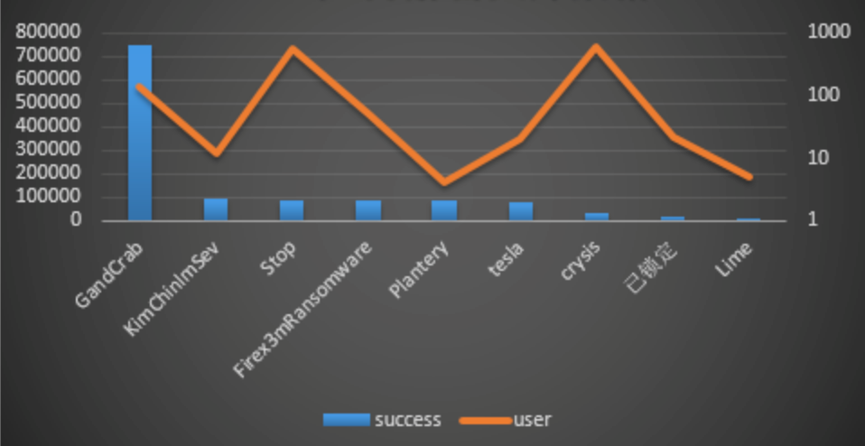
From the statistics of the decryption tool in this month, GandCrab is the largest decryptor, followed by KimChinInSev; the highest number of users who use the decryption master to decrypt files is still the Infected device of the Stop family, followed by Crysis Infected equipment of the family.
Summary
Attacks against servers are still a major direction of current ransomware. Enterprises need to strengthen their own information security management capabilities-especially weak passwords, vulnerabilities, file sharing and remote desktop management, in order to respond to the threat of ransomware. Here are some suggestions for administrators:
- Multiple machines, do not use the same account and password
- The login password should be of sufficient length and complexity, and the login password should be changed regularly.
- The shared folder of important data should be set up with access control and be backed up regularly
- Regularly detect security vulnerabilities in the system and software and apply patches in a timely manner.
- Check the server regularly for abnormalities. View scope includes:
(1) Is there a new account
(2) Whether the guest is enabled
(3) Is there an exception in the Windows system log?
(4) Is there any abnormal interception of antivirus software?
- Install security software and make sure it works properly.
- Download and install software from regular channels.
- For unfamiliar software, if it has been intercepted by antivirus software, do not add trust to continue running.
In addition, neither corporate victims nor individual victims are advised to pay ransom. Paying ransom not only encourages ransomware in disguise, but the decryption process may also bring new security risks.
Many common ransomware only encrypt the file header data. For some types of files (such as database files), you can try to recover some of the losses through data repair methods. If you have to pay the ransom, you can try to negotiate with the hacker to reduce the ransom price. At the same time, during the negotiation process, you should avoid exposing your true identity information and urgency, so as to avoid the hacker asking for higher price.
Learn more about 360 Total Security