The spread of the ransomware poses a serious security threat to businesses and individuals. 360 Security Center has conducted a full range of monitoring and defense against ransomware. New ransomware families this month include DoppelPaymer, Teslarvng and One-OAPlugins, etc.
360 Decryption Tool added decryption support for DiskParasite ransomware family in March 2020.
Infection data analysis
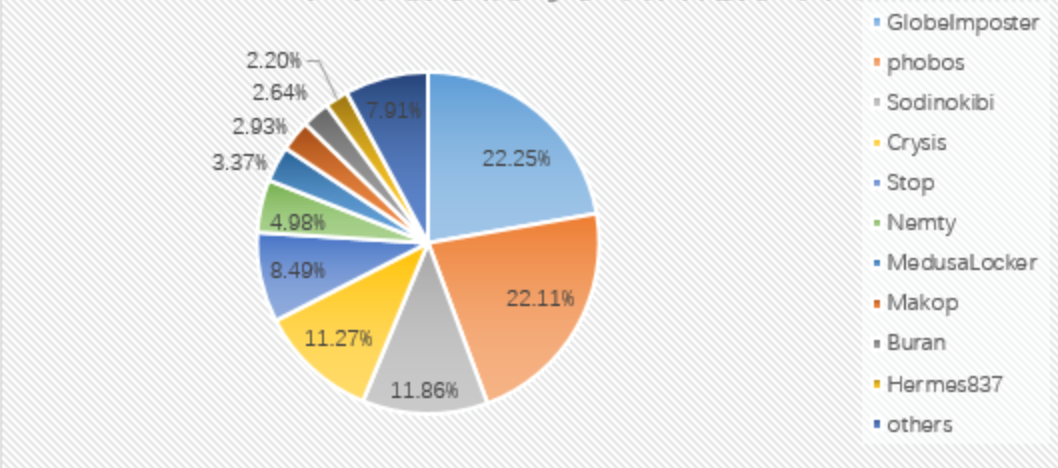
Analysis of the proportion of ransomware families this month: GlobeImposter took the first place with 22.25%; followed by phobos with 22.11%; the Sodinokibi family ranked third with 11.86%. The proportion of Makop, a newly emerging ransomware, has risen significantly-this once unknown ransomware jumped directly to No. 8 on the list this month.
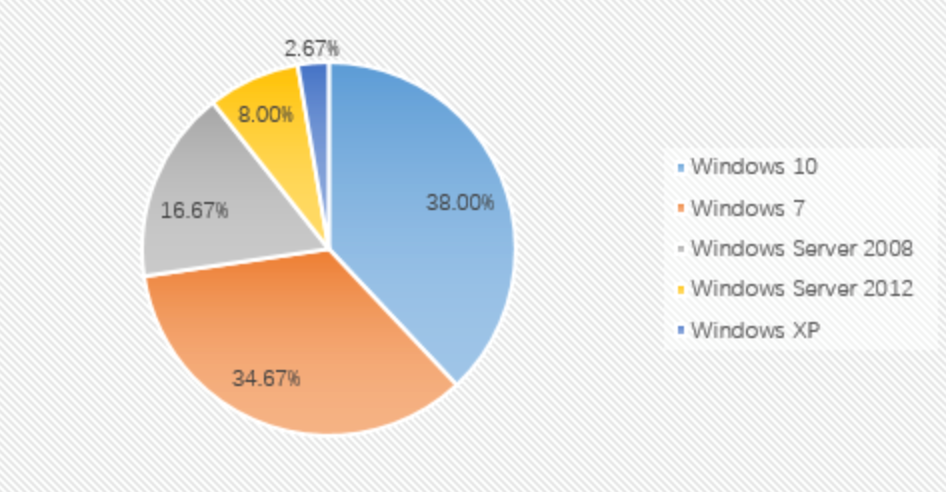
From the perspective of the proportion of infected systems: the top three systems this month are still Windows 10, Windows 7 and Windows Server 2008. As in February, the share of the Windows 10 operating system continues to exceed Windows 7.
Desktop systems and server systems accounted for the majority of infected systems in March, with desktop systems still accounting for an absolute majority. Compared with last month’s statistics, there has been no significant fluctuation.
In addition, we also paid attention to the user feedback of the ransomware section of the 360 Forum in February 2020.
(https://bbs.360.cn/forum.php?mod=forumdisplay&fid=7592):
In this month, the forum reported a total of 77 cases involving 19 families and helped some of them decrypt.
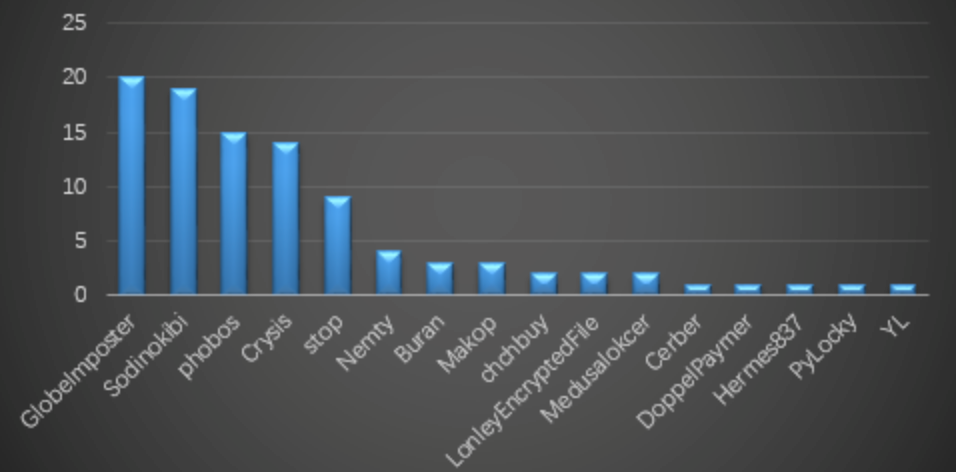
The three families with the most feedback are: GlobeImposter, Sodinokibi and phobos. New families / variants added in feedback include: Crysis (modified file suffix iu21j, eight), DoppelPaymer (modified file suffix doppeled, how2decrypt.txt), Teslarvng (modified file suffix yakuza), Stop (modified file suffix npsk, remk) etc.
Teslarvng Ransomware Family
The Teslarvng ransomware is a new ransomware emerging this month. Due to the small amount of domestic transmission, it has not attracted widespread attention for the time being. The ransomware is spread through common weak password attacks (brute cracking and manually poisoning after obtaining the remote desktop password).
The ransomware will fill in “\ x93 \ x9F \ x7B \ xA9” at the end of each encrypted file, and write the files with encryption success and encryption failure to the \\ Adobe \\ Extension Manager CC \\ Logs directory c.txt and fails.txt files.
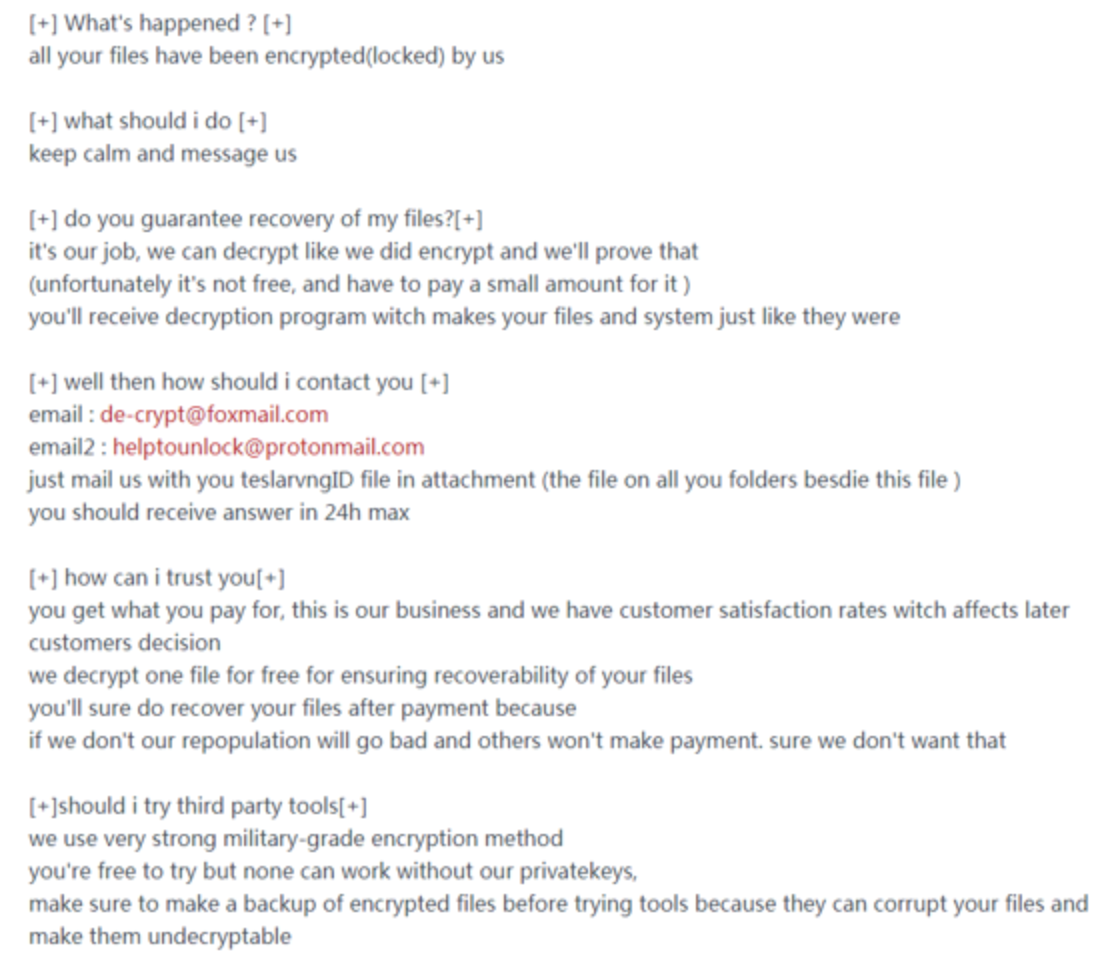
Like most ransomware viruses, this virus also allows users to contact the hacker through the mailbox left in the ransom note and modify the file suffix to .Teslarvng. The ransomware also appeared a new variant this month, modifying the file suffix to .yakuza.
Nemty Ransomware Family
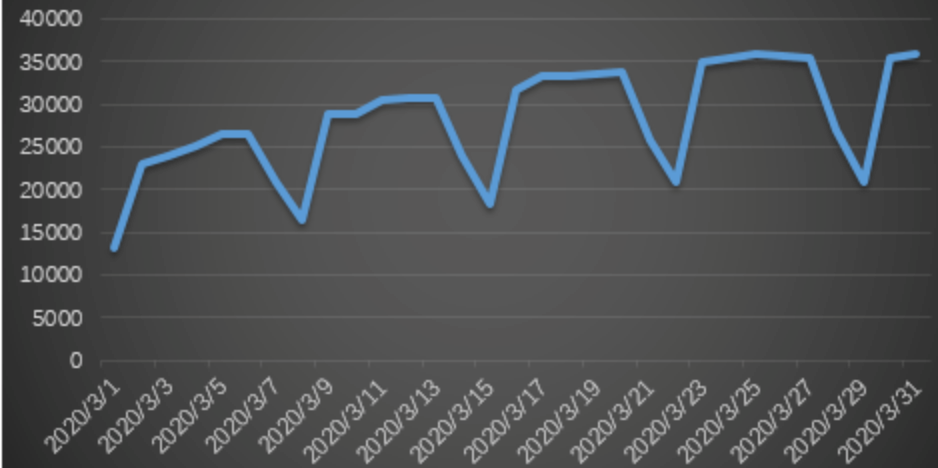
In mid-March, 360 Security Center monitored that the Nemty ransomware began to spread using U-disk worms. This channel was first used by the GandCrab ransomware family in November 2019 and infected a large number of devices. In this month, the amount of worm attacks has been on the rise, and from the situation graph, we can see that the worm is more affected by working hours, and there will be a large decrease in the amount of attacks during the weekend. However, the overall situation in March was still rising.
One-OAPlugins Ransomware Family
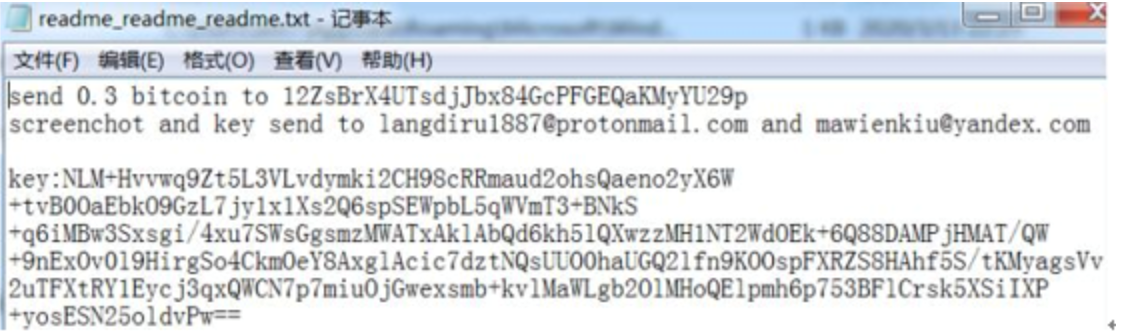
360 Security Center detected that a ransomware was spread using the file upload vulnerability of the OA system this month. After encrypting the file, the ransomware will add a number 1 to the end of its suffix and leave a ransom letter asking users to pay 0.3 Bitcoin ransom.
The following is the hacker mailbox information collected this month:
System security data analysis
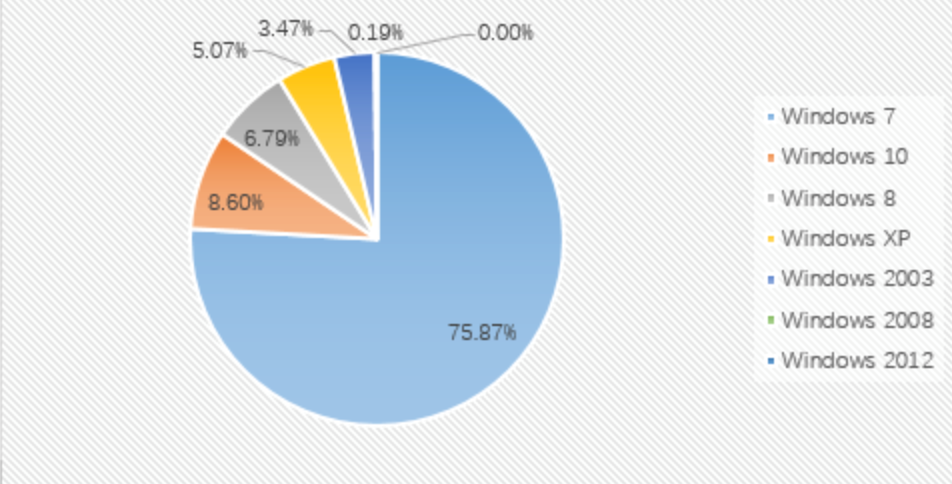
By comparing the data of February and March 2020, it is found that the proportion of each system has not changed much this month. The top three are still Windows 7, Windows 8 and Windows 10.
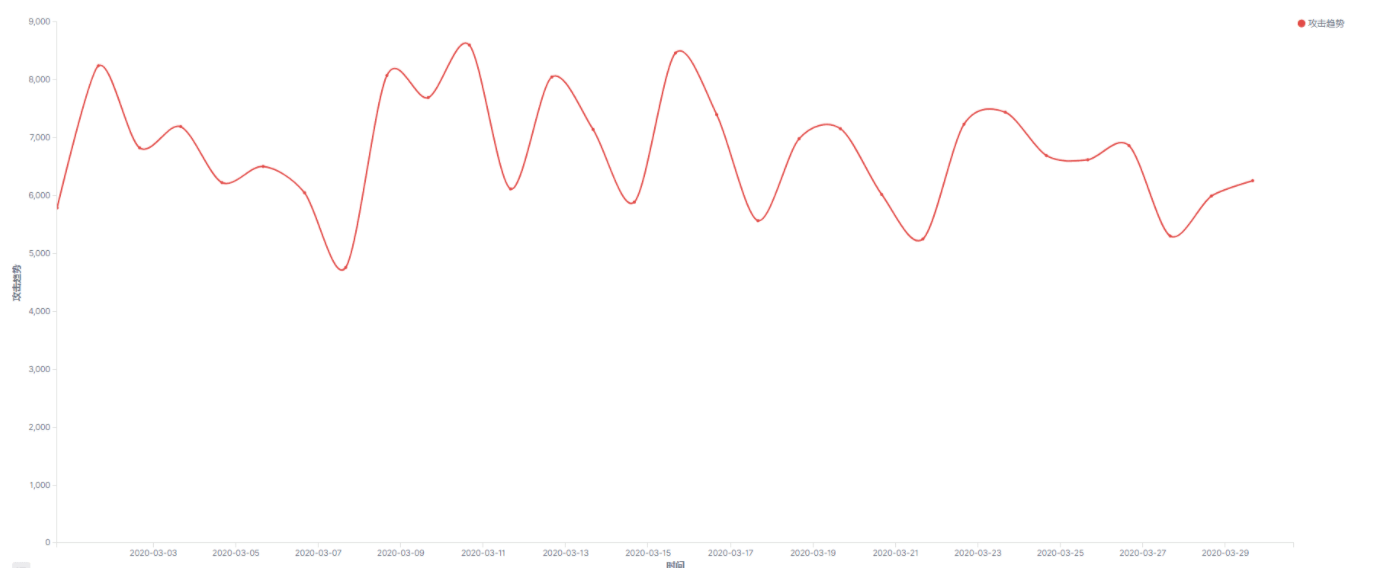
Analysis of the weak password attack situation in March 2020 revealed that Mssql’s weak password attack had two peaks in the middle of the month. Rdp and Mysql weak password attacks did not fluctuate as a whole this month.
The following figure shows the overall trend of using Mssql to attack the system. The data for the entire month is relatively stable without much fluctuation.
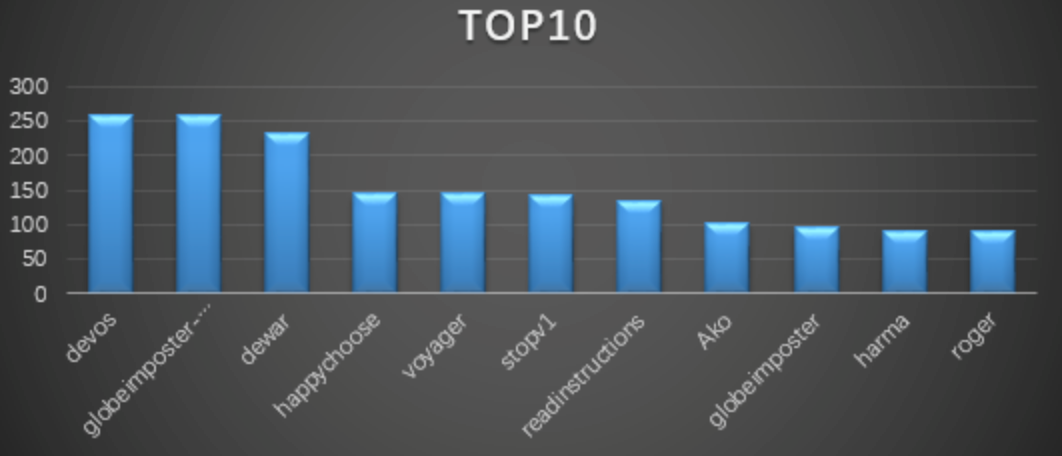
Ransomware keywords
The data comes from the search statistics of lesuobingdu.360.cn. (Excluding WannCry, AllCry, TeslaCrypt, Satan, Kraken, Jsworm, X3m and GandCrab families)
Devos: belongs to the phobos ransomware family. Since encrypted files will be modified by devos and become keywords, the ransomware mainly violently cracks remote desktop passwords. After getting the passwords, they will manually spread the virus.
l globeimposter-alpha865qqz: belongs to the GlobeImposter ransomware family. Because the encrypted file suffix will be changed to happychoose to become a keyword, the ransomware mainly cracks the remote desktop password by blasting, and manually spreads the virus after getting the password.
l dewar: same as devos
l Happychoose: Same as globeimposter-alpha865qqz.
l Voyager: belongs to the Hermes837 ransomware family, and because the file is encrypted, it will be modified into a voyager and become a keyword. The ransomware family mainly cracked remote desktop passwords by brute force, and then spread the virus manually after successful.
l Stopv: For the Stop family, there are many variants of the ransomware virus, which are spread through cracking software or activation tools.
l Readinstructions: belonging to the MedusaLocker ransomware family, also known as the “Medusa” ransomware virus, the ransomware mainly violently cracks remote desktop passwords, gets the passwords and spreads the virus manually.
l Ako: belongs to the Ako ransomware family. The ransomware is mainly spread through spam and violently cracking remote desktop passwords and manually poisoning.
l Globeimposter: Same as globeimposter-alpha865qqz.
l Harma: belongs to the Crysis ransomware family, because the file will be modified to ncov after being encrypted and become a keyword. The ransomware family mainly cracked remote desktop passwords by brute force, and then spread the virus manually after successful.
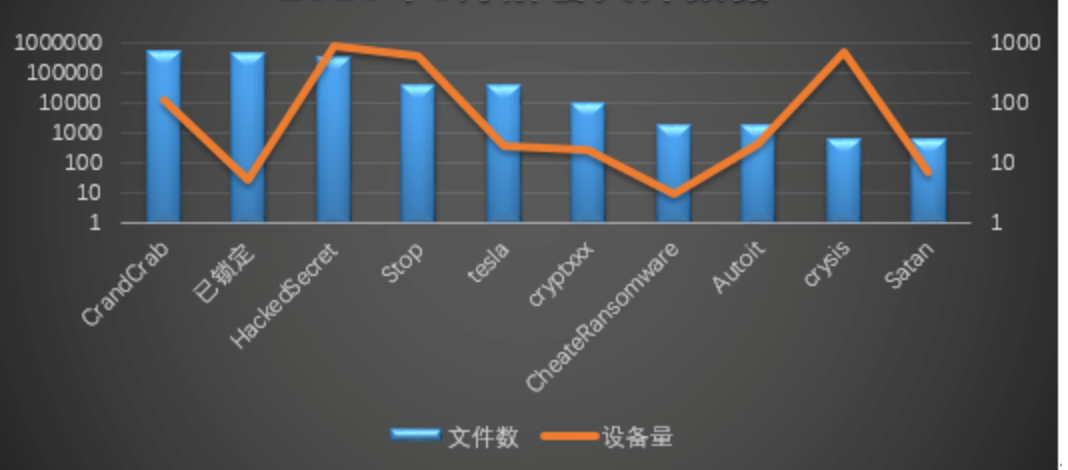
Decryption Tool
Judging from the decryption data of the decryption tool this month: the largest number of decrypted files is still GandCrab, followed by “locked”; and from the dimension of the number of successful devices seeking decryption, the most is the HackedSecret family, followed by the Stop family.
Summary
Ransomware attacks against servers are still a major direction of ransomware. Companies need to strengthen their information security management capabilities-especially weak passwords, vulnerabilities, file sharing, and remote desktop management to respond to the threat of ransomware Here we give some suggestions to administrators:
1. Multiple machines, do not use the same account and password
2. The login password should be of sufficient length and complexity, and the login password should be changed regularly
3. The shared folder of important data should be set with access control and regular backup
4. Regularly detect security holes in the system and software and apply patches in a timely manner.
5. Check the server regularly for abnormalities. View range includes:
(1) Is there any new account
(2) Whether Guest is enabled
(3) Is there any abnormality in the Windows system log?
(4) Whether the anti-virus software has abnormal interception
6. Install security software and ensure that it runs normally.
7. Download and install software from regular channels.
8. For unfamiliar software, if it has been intercepted by anti-virus software, do not add trust to continue running.
In addition, neither corporate victims nor individual victims are recommended to pay a ransom. The payment of ransom not only encourages blackmail attacks in disguise, but the decryption process may also bring new security risks.
For common ransomware, many of them only encrypt the file header data. For some types of files (such as database files), you can try to recover some of the losses through data repair. If you have to pay the ransom, you can try to negotiate with the hackers to reduce the ransom price. At the same time, you should avoid exposing your true identity information and urgency during the negotiation process to avoid hackers asking for prices. Since most decryption service companies purchase key decryption files by contacting hackers, try to avoid consulting too many third-party decryption companies (consulting too many third-party decryption companies is equivalent to consulting multiple hackers, which may cause hackers to increase their prices.)
Learn more about 360 Total Security