In early October, the world’s largest manufacturer of hearing aids, Denmark’s Demant was invaded by ransomware and directly lost as much as $100 million. The violent offensive of the ransomware wave followed the wave. On October 17th, global shipping giant Pitney Bowes also suffered Ransomware attack, 90% of Fortune 500 companies are affected.
Although the attacks of the two giants are not the same virus, the ransomware is still a major threat to cybersecurity. The following is an analysis of the 360 security center’s overall infection situation in October.
Topstream family GlobeImposter returns to the top
In the past October, the major ransom virus family launched an invasion war, and the “top-flow family” GlobeImposter accounted for 18.37% this month, and once again reached the summit, the “play rate” was long-lasting; secondly, “new online red” The phobos family and the Crysis family ranked second and third respectively with 16.78% and 15.87%. On the contrary, the Stop family has begun to show signs of decline from 22.9% in September to 9.52% this month.
The Proportion of Ransomware Family in October 2019
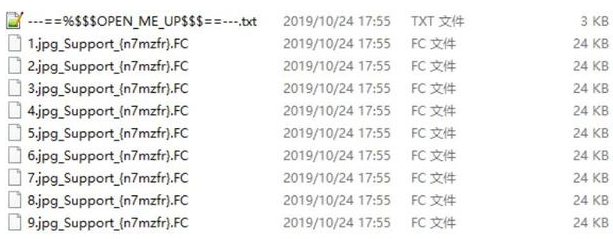
Among the top ten families in October, the FakeParadise virus is worth watching. FakeParadise can be described as “novice” in this month, but driven by interest, its extortion price is as high as $1995 for bitcoin, and ransom is converted to more than 10,000 yuan. FakeParadise will modify the file suffix to _Kim ChinIm_{ID}.sev and Support_{ID}.FC, but 360 Security Center has cracked the ransomware in the first time in China.
File encrypted by FakeParadise ransomware
As for the reason for FakeParadise naming, in foreign countries, it is classified into the Paradise family, but the 360 security center found that the two use the encryption method is significantly different, FakeParadise is written in C++ language, while the traditional Paradise uses Written in C# language.
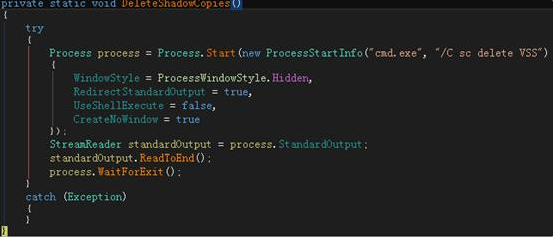
In addition, in order to counter the system’s file recovery function, FakeParadise will call the system command to delete the shadow. This is also different with the traditional Paradise. The Paradise family ransomware will delete the system’s Volume Shadow Copy (VSS: Volume Shadow Copy), but Existing shadows won’t be deleted (so files can be recovered from the system’s restore point). In addition, there are many different types of ransomware information styles and encryption algorithms in the two families.
FakeParadise removes shadows
Paradise only removes the shadow service
Win10 system “gradually lost”, botnet pushes high password attack
As for system infections, 360 Security Center monitoring found that the top three systems this month are still Windows 7, Windows 10 and Windows Server 2008. As Windows 10 gradually becomes mainstream, its attack share has also increased by about 5%. In the foreseeable future, Win10 users who are gradually becoming “attacking the bull’s eye” need to be vigilant.
The proportion of infected systems in October 2019
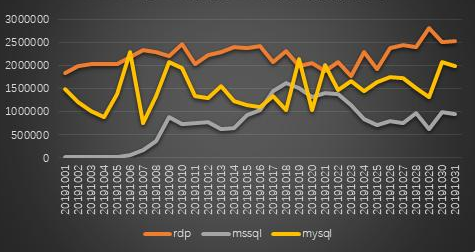
In addition, 360 Security Center discovered through the trend of weak password attacks in October that the attack trend of MsSQL had significant growth on October 6th and October 8th, mainly due to the MyKings hacking organization from October 6th. Increasing its attack input, in addition to frequently updating the communication address of the bot, it also launched a new round of brute force attacks against the MsSQL database, with the intention of controlling more servers to form a larger mining botnet.
Weak password attack trend chart for October 2019
Hacker mailbox disclosure
The following is the hacker email information collected by the 360 security center this month:
| John_Gilbert_2019@protonmail.com | recoveryqq@protonmail.com | helpme.parner@yahoo.com |
| zigger@protonmail.com | sercurityteacher@cock.li | gerentosrestore@firemail.cc |
| DataBack@qbmail.biz | zzzoruda@cock.li | getbtc@aol.com |
| starter@cumallover.me | sicck@protonmail.com | emerson.parkerdd@aol.com |
| btcpay1@protonmail.com | sosca@foxmail.com | easydecrypt555@cock.li |
| proansw@protonmail.com | mrcrypting@airmail.cc | DecrypterSupport@cock.li |
| Folieloi@protonmail.com | backupyourfiles@420blaze.it | decoding@qbmail.biz |
| Ctorsenoria@tutanota.com | b1tc01n@aol.com | deadmin@cock.li |
| sambolero@tutanoa.com | Blackmax@tutanota.com | davidharris@nuke.africa |
| rightcheck@cock.li | cryptocash@aol.com | cyb3rcrypt@protonmail.com |
| crypt2020@outlook.com | vivaldicrypt@outlook.com | cobian0ransom@cock.li |
| cryptt2020@protonmail.com | newebola@aol.com | cobian_ransom@protonmail.com |
| getmyfilesback@airmail.cc | rsa1024@tutanota.com | cobain0ransom@cock.li |
| koreadec@tutanota.com | mrcrypt@cock.li | cobain_ransom@protonmail.com |
| vourrealdecrypt@airmail.cc | jsmith1974@mail.fr | cleverhorse@xmpp.jp |
| filedecryptor@nuke.africa | decryptbots@cock.li | butters.felicio@aol.com |
| mr.brozer@protonmail.com | dfvdv@tutanota.com | btcthebtc@aol.com |
| ticketbit@tutanota.com | relvirosa1981@aol.com | betasup@mail.ee |
| ticketbit@mailfence.com | stoneland@firemail.cc | ashleyqz5tfmoore@aol.com |
| 1701222381@qq.com | raceso@qq.com | alcorestore@protonmail.com |
| yourdatahere@tutanota.com | Hariliuios@tutanota.com | advancedbackup@protonmail.com |
| xmedusax@cock.li | kazkavkovkiz@cock.li | admin@fentex.net |
| whitwellparke@aol.com | patern32@protonmail.com | supdec@8chan.co |
| wewillhelp@xmpp.jp | veracrypt_restore@protonmail.com | helpdesk_nemty@aol.com |
| wewillhelp@ctemplar.com | upeditco@gmail.com | elzmflqxj@tutanota.de |
| tirrelllipps@aol.com | unlock01@protonmail.com | fullrestore@qq.com |
| symetrik@protonmail.com | lockers123@protonmail.com | steamgamer99@gmail.com |
| servers70@tutanota.com | buttersfelicio@aol.com | corpseworm@protonmail.com |
| savignythayne@chadfarrcreations.com | partfile@airmail.cc | fidelio.bartyn@aol.com |
| savefiles@cock.li | hmdjam@protonmail.com | churiladr@cock.li |
| restoringbackup@airmail.cc | husilusi@cock.li | salesrestoresoftware@firemail.cc |
| recoverydata54@protonmail.com | paybuyday@aol.com | salesrestoresoftware@gmail.com |
| recoverunknown@aol.com | amundas@firemail.cc | admin@slide.best |
| recover_file13@protonmail.com | decryptmyfiles@qq.com | bitlocker@foxmail.com |
| rdp800@rape.lol | mrimrssmith@cock.li | btccrypthelp@cock.li.com |
| professionalhelp@india.com | mrimrssmith@protonmail.com | dataforcoin@aol.com |
| onlyiwillhelpyou@protonmail.com | mrimrssmith@cock.lki | writehere@onlinehelp.host |
| mrcrypting@protonmail.com | addison_jimmy@aol.com | xisdxi@cock.li |
| merlinstusan@protonmail.com | bitlock@foxmail.com | cybercrypt@cock.li |
| LiberLover@tutanota.com | btcpayment@airmail.cc | willyhill1960@protonmail.com |
| konte@cock.li | china_@tol.com | willyhill1960@tutanota.com |
| keysfordecryption@airmail.cc | china_helper@aol.com | Bdataforcoin@aol.com |
| icanhelpu@cock.li | china.helper@india.com | back_me@foxmail.com |
| securityteacher@cock.li | china989helper@protonmail.com | admin@sectex.net |
| theonlyoption@jabb3r.de | china989helper@redchan.it | admin@fentex.world |
| welcokaj@nuke.africa | dataforcoin@cock.li | Killback@protonmail.com |
| unlock@goldenbay.su | decrypthelper2020@protonmail.com | bitlocker@hotmail.com |
| unlock@graylegion.su | goretosrestore@firemaill.cc | gillamlowrance@aol.com |
| vacandeli1971@protonmail.com | hibbard_r@ferepot.info | inspectionguard@cock.ii |
| nmode@tutanota.com | ihelpyoudecrypt@protonmail.com | kickclakus@protomail.com |
| maximum@onlinehelp.host |
All kinds of hackers attacked and attacked the virus, which caused a serious threat to users’ security. As the world’s largest and most effective ransomware decryption tool, 360 decryption tools can support more than 300 kinds of ransomware decryption, and powerfully protect user data and property security.
Security advice:
In the face of the escalating ransomware epidemic situation, 360 security brains recommend that users improve their network security awareness, strengthen information management, or do the following defenses to protect computer privacy and property security:
1, As soon as possible, go to http://www.360totalsecurity.com download and install 360 Total Security, and comprehensively intercept all kinds of ransomware attacks;
2, enterprise server administrators try to avoid multiple machines using the same account password, to ensure the complexity of the login password, and to do regular replacement;
3, The shared folder of important data should be set with access control and regular backup; regularly detect security vulnerabilities in the system and software, and timely patch;
4, individual users should download and install software from the formal channels, use a variety of activation tools with caution; for unfamiliar software, if it has been intercepted by anti-virus software, do not add trust to continue running;
5, When encountering emails sent by strangers, be cautious and try to avoid downloading attachments. If you need to download, you must first check the accessories with security software.
6, after recruiting ransomware, please install the “360 Total Security decryption tool” function, click “Scan now” to recover the encrypted file.
Learn more about 360 Total Security